ISO 27001, also known as the International Organization for Standardization (ISO) 27001, is a globally recognised standard for information security management systems (ISMS). It provides a systematic and structured approach for organisations to manage the security of their valuable information assets.
Since the release of ISO 27001:2022 on 25th October 2022, here are some questions that you may have:
Question 1: ISO 27001 Is New To Me, And I Want My Organisation To Be Certified To It.
For organisations that are not yet certified to ISO 27001, we recommend that your organisation go for the latest ISO 27001:2022 version now!
Find out more about ISO 27001 here!
Question 2: My Organisation Is Currently Certified To ISO 27001:2013, With An Upcoming Surveillance Audit This Year. What Should I Be Doing?
Note: Existing ISO 27001:2013 certification will be valid till 25th October 2025.
Organisations should start taking steps to transition into the latest ISO 27001:2022. This includes incorporating the new requirements, where organisations can consider adopting a phased approach.
- Conduct a gap assessment of existing processes against the latest ISO 27001:2022 requirements and identify any gaps.
- Remediate these gaps in the form of additional/update of existing documentation (e.g. policies) or update/establish new processes.
- Reach out to your certification body regarding your interest in certifying against ISO 27001:2022 prior to your surveillance audit.
By systemically addressing the gaps, organisations can better ensure a smooth transition to the new standard and enhance their information security practices.
In this blog post, we will delve into some controls that have gained significant emphasis in ISO 27001:2022. Focused on crucial aspects such as Cloud Services, Data Privacy and Protection, and Network Security, these controls are essential to address modern cybersecurity challenges today.
Revised from ISO 27001:2013 – Information Security – Information Security Management Systems – Requirements.
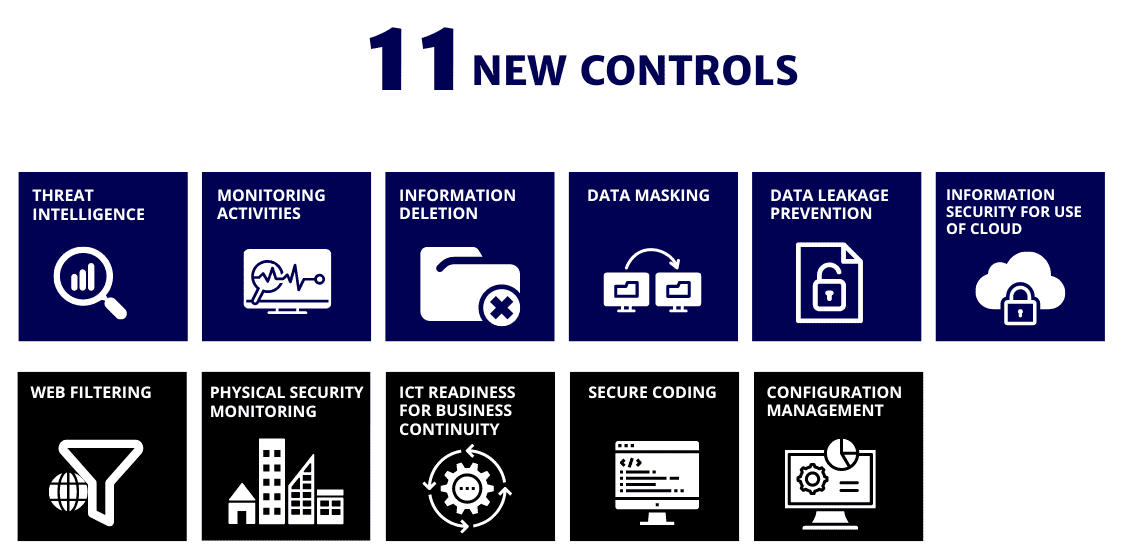
The latest version includes 11 new controls, of which six have gained significant emphasis due to their increased focus on Cloud Services, Data Privacy and Protection and Network Security. As for the other five new controls, they primarily necessitate enhancements to existing processes and documentation in the 2013 version of ISO 27001.
| Topic | Annex A Control |
|---|---|
| Usage of Cloud Services | 5.23 Information Security for use of Cloud Services |
| Data Privacy and Protection |
8.10 Information Deletion 8.11 Data Masking 8.12 Data Leakage Prevention |
| Network Security |
5.7 Threat Intelligence 8.16 Monitoring Activities |
Use of Cloud Services
With the boom in cloud services since the early 2010s continuing to this day, businesses across various industries are increasingly seeking to leverage the benefits of cloud computing for enhanced agility, efficiency, and innovation. The increased usage of cloud services has revolutionised how organisations store, access, and manage their data. With the increased reliance on such operational technologies and services, it is imperative for organisations to understand and manage the information security risks associated with their usage of cloud services.
Sharing sensitive data with third-party cloud providers introduces new vulnerabilities and potential threats to organisations. Thus, it is crucial for organisations to comprehensively assess and mitigate the risks, ensuring the confidentiality, integrity, and availability of the organisation’s data.
So … How/where can I start?
- Understand, evaluate, and manage the potential information security risks posed by the usage of Cloud Services within your business environment.
- Establish a topic-specific policy on the usage of Cloud Services (e.g. Cloud Security Policy) or update existing policies on 3rd Party/Vendor Management to extend its scope and guidelines to include cloud vendors.
- Establish guidelines on the security requirements of cloud vendors as part of your procurement process (and update your Procurement/any other relevant policy while you are on it!)
Data Privacy and Protection
Learning from cyber incidents like the Kaseya supply chain attacks, regulators and international bodies recognises the importance of managing risks associated with third-party service providers through a comprehensive approach. By conducting thorough assessments, organisations will need to identify the relevant third-party risks to their systems and data. This includes performing thorough due diligence, monitoring the security posture of third parties, and establishing clear contractual terms and conditions to address security requirements.
So … How/where can I start?
- Understand the legal, statutory, regulatory, and contractual requirements towards the deletion of data/information that the organisation stores.
- Understand where these data/information are stored.
- Are they soft copies or physical copies?
– Are they hosted on-premise or in-cloud? - Understand how these data/information are being stored.
– What techniques are utilised to protect the privacy of the PII/sensitive data? - Understand who has access and how is access to this data/information being provisioned and monitored.
- Understand if there are data backups to this data/information and how is access to these backups being provisioned and monitored.
- Establish deletion methods for the various types of data/information stored.
– How secure and effective are the methods in ensuring that the stored data are permanently removed? - Establish measures to avoid unauthorised disclosure of sensitive information.
– What are the ways that tese data can be exfiltrated from the organisation?
– Are there sufficient controls in place to prevent anyone and identify them when needed?
Knowing the enemy is half the battle won.
Sun Tzu, Author of The Art of War
Network Security
Understanding your adversaries is crucial in the battle for security. To effectively protect your business and operating environment, it is essential to comprehend the threat landscape.
According to Crowdstrike’s 2023 Global Threat Report, the average breakout time for interactive eCrime intrusion activity has shortened from 98 minutes in 2021 to 84 minutes in 2022. This highlights the alarming speed at which threat actors can infiltrate your cloud environment, gain unauthorised access, steal, or delete data, all while remaining undetected. Hence, it is imperative for organisations to prioritise the identification and proactive monitoring of potential security incidents, preventing their escalation into actual breaches.
So … How/where can I start?
- Consider subscribing to security newsletters, advisories, bulletins by reputable vendors and security communities to keep yourself up to date to the latest trends.
- Get involved in security forums.
- Establish partnerships with other organisations and security vendors.
- Identify critical systems where monitoring efforts should be focused on
- Establish baselines for monitoring efforts.
- Establish baselines for reporting events and incidents.
conclusion
Since its inception, the ISO 27001 standard continues to serve as a valuable guide for establishing an effective Information Security Management System (ISMS). While there are necessary requirements for certification, it is crucial that organisations avoid being overly fixated on mere compliance. Instead, the focus should be on understanding the intent and purpose of the standard.
Fostering a continuous improvement process and encouraging a proactive stance towards security, the adoption of an ISO 27001:2022 standard is highly beneficial to organisations in today’s dynamic and evolving cybersecurity landscape. By establishing an ISO 27001-certified Information Security Management System (ISMS), organisations can better adapt and strengthen their security measures, effectively address emerging threats and safeguard their crown jewels.
At Privasec, we have a Governance, Risk and Compliance (GRC) team of highly experienced and certified professionals, each with an average of 10 years of cyber security consulting experience. With great expertise and a commendable proven track record of implementing an Information Security Management System (ISMS) certifiable to ISO 27001, we are glad to assist and support organisations in their standards adoption journey.
Author:
Eugene Nah, GRC Security Consultant
Eugene is currently a Security Consultant in the GRC Team. With experience in implementing a SaaS GRC platform within the APAC region, he advised clients on best practices to manage and mature their Cybersecurity, Risk Management and Compliance capabilities. Eugene also has extended experiences and expertise in advising clients across multiple industries, particularly in the space of ISO 27001, Data Privacy (PDPA) and NIST CSF.
Related Posts:
Secure your business with us
Simply drop us an email at [email protected] or call us at +65 6610 9597 (SG) / 1800 996 001 (AU) for more details