Cloud Security Assessments
Privasec is now a Sekuro Company
Cloud Security Assessment
Privasec, A Sekuro company’s Cloud Security Assessment service is the ideal first step for any organisation adopting cloud technologies as part of their business strategy. Cloud Service Providers operate on a ‘Shared Security Model’ whereby the lower end of the technology stack is secured, monitored and maintained by the vendor, leaving the upper end of the stack to be secured by the organisation.
Although the responsibility of confidentiality, integrity and availability of data in the cloud is shared between the provider and organisation, the responsibility split is far from even. Using the ‘Iceberg’ analogy demonstrates how much of the responsibility falls onto the organisation.
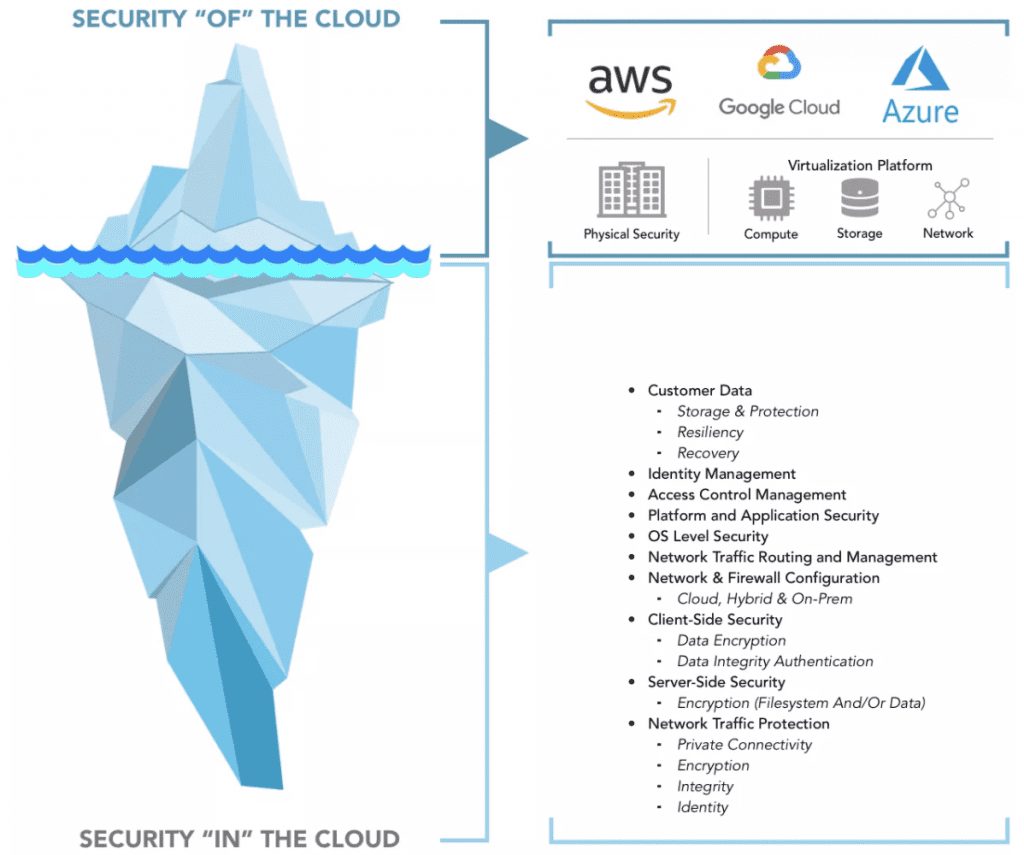
This can be a daunting task for any organisation to undertake, even those with ready access to skilled cloud security engineers.
Privasec, A Sekuro company’s Security Consultants have extensive experience with Cloud Security good practices and have helped numerous clients secure their cloud environments across multiple vendors. Using industry best-practices and best-of-breed assessment technology, Privasec is able to harness the power of the cloud using cloud-native functionality to rapid perform security & configuration assessments across thousands of cloud security configurations.
Privasec, A Sekuro company’s Cloud Security Assessments provide you with detailed visibility in your cloud security posture and in-depth risk analysis into various components including:
- Identity & Access Management;
- Roles and Policies;
- Enterprise Communications;
- Data Integrity & Confidentiality;
- System Redundancy;
- Workloads & Applications;
- Data Storage;
- Databases;
- Network & Routing; and
- Container, Serverless and FaaS Security.
Privasec, A Sekuro company Cloud Security Assessments provide clear, concise, actionable intelligence to business stakeholders about the current state of their cloud security posture and valuable insight on how to protect the organisation in the cloud.
Your Cloud Security Assessment Report includes:
- An executive summary detailing our scope, approach and summary findings and recommendations. This section is aimed at the executive management and contains summarised, non-technical descriptions of cloud security issues alongside a business interpretation of the key business security risks.
- Detailed findings and observations section which includes the detailed assessment findings, the business security risks from identified security issues discovered by the team, as well as recommendations on how best to mitigate these risks.
- Detailed recommendations will be based on industry best practice security recommendations to maintain the confidentiality, integrity and availability of the systems and information assets in the cloud.
The Importance of Cloud Security Assessments
Ensuring the security of data stored and processed in the cloud is essential to protect against cyber threats, comply with regulatory requirements, and maintain customer trust. Here’s why conducting thorough cloud security assessments is crucial for organisations operating in the cloud.
1. Protection of Sensitive Data:
Conducting a cloud security assessment is essential to safeguard sensitive data stored and processed in cloud environments. Assessments help identify vulnerabilities and weaknesses in cloud infrastructure, applications, and configurations that could potentially expose sensitive information to unauthorised access or breaches.
2. Compliance with Regulations:
A thorough cloud security assessment ensures that organisations comply with relevant regulations such as the Payment Card Industry Data Security Standard (PCI DSS), reducing the risk of non-compliance penalties and legal liabilities.
3. Mitigation of Security Risks:
Cloud environments are susceptible to various security threats, including data breaches, malware attacks, and insider threats. By conducting regular security assessments, organisations can proactively identify and address security risks before they escalate into serious incidents, minimising the likelihood of data breaches and business disruptions.
4. Assurance of Data Integrity and Availability:
Ensuring the integrity and availability of data stored in the cloud is critical for business continuity and maintaining customer trust. Cloud security assessments help organisations verify the reliability of cloud service providers’ infrastructure, data replication processes, and disaster recovery plans, ensuring data integrity and availability in the event of hardware failures or natural disasters.
5. Strengthening of Security Posture:
Continuous evaluation and improvement of cloud security measures are vital to adapt to evolving cyber threats and vulnerabilities. Cloud security assessments provide valuable insights into the effectiveness of existing security controls and enable organisations to implement additional measures to strengthen their security posture and resilience against emerging threats.
A Step-by-Step Guide to Cloud Security Assessments
Cloud security assessments are a systematic approach to evaluating and enhancing the security of cloud infrastructure, applications, and data. Here’s a step-by-step guide to the process of securing the cloud.
1. Initial Assessment and Scoping:
The first step in the cloud security assessment process involves conducting an initial assessment to define the scope of the assessment, identify key stakeholders, and determine the objectives and goals. This phase includes gathering information about the organisation’s cloud infrastructure, applications, data, and security policies.
2. Risk Identification and Analysis:
Next, the assessment team identifies and analyses potential security risks and vulnerabilities in the cloud environment. This includes assessing threats such as data breaches, unauthorised access, malware attacks, and insider threats, as well as evaluating the effectiveness of existing security controls and measures.
3. Compliance Evaluation:
Organisations must comply with various regulations and standards governing data protection and privacy when operating in the cloud. During this phase, the assessment team evaluates the organization’s compliance with relevant regulations and industry-specific standards. Any compliance gaps are identified and addressed accordingly.
4. Security Controls Assessment:
The assessment team examines the effectiveness of security controls and measures implemented in the cloud environment to mitigate identified risks. This includes assessing access controls, encryption mechanisms, authentication processes, data backup and recovery procedures, and monitoring and logging practices.
5. Reporting and Recommendations
Finally, the assessment team compiles the findings and recommendations into a comprehensive report detailing the identified security risks, compliance gaps, and areas for improvement. The report includes actionable recommendations and best practices to enhance cloud security, mitigate risks, and strengthen the organisation’s overall security posture.
Why Choose Privasec, A Sekuro company for Cloud Security Assessments?
FAQs about Cloud Security Assessments
Cloud security assessments should be conducted by experienced cybersecurity professionals or specialised security firms with expertise in cloud security. These professionals have the knowledge and tools to perform thorough assessments and provide actionable recommendations to improve cloud security.
The frequency of cloud security assessments depends on factors such as the organisation’s risk tolerance, regulatory requirements, and changes to the cloud environment. Generally, organisations should conduct assessments regularly, at least annually or whenever significant changes are made to the cloud infrastructure or applications.
A cloud security assessment typically includes evaluating the organisation’s cloud architecture, access controls, data encryption practices, identity and access management (IAM) policies, network security configurations, logging and monitoring mechanisms, and compliance with relevant regulations and industry standards.
The duration of a cloud security assessment can vary depending on factors such as the size and complexity of the cloud environment, the scope of the assessment, and the availability of resources for conducting the assessment. Typically, assessments can range from a few weeks to several months.
We provide the best service in industry
Our team of experienced Governance, Risk and Compliance (GRC) consultants can help assess and support your organisation’s cyber security strategy.