A traditional penetration test in Singapore often relies on information provided by the client, creating a limited scope that mimics a guided attack. But real-world attackers rarely have such roadmaps. They operate with limited initial knowledge, starting with the name of a target organisation and leveraging the power of Open-Source Intelligence (OSINT) to piece together information and unearth hidden entry points. This is where External Perimeter Penetration Testing (EPPT) steps in, leveraging the power of OSINT to deliver a more realistic and comprehensive assessment.
The Role of OSINT: Unveiling the Unseen
Attackers operate in a realm of unknowns, piecing together fragments of information gathered from various sources. OSINT becomes a vital weapon here in the penetration tester’s arsenal, empowering them to see what’s unseen.
Traditional protocols during a penetration test rely on a predefined list and might cause testers to overlook crucial assets. However, through meticulous OSINT investigations, a tester could discover its existence. For example, sensitive information pertaining to a particular organisational process might be exposed in an employee’s LinkedIn or social post. This proactive discovery reveals an unexpected attack vector, providing invaluable insights into the organisation’s real-world security posture.
Here's how OSINT empowers penetration testers:
1. Asset Discovery
One of the initial steps is identifying all assets within the organisation’s network, which exposes potential attack vectors missed by client-provided lists when conducting a traditional penetration test. OSINT techniques enable testers to scour the internet for publicly available information about the organisation, such as domain names, IP addresses, subdomains, and employee information. By leveraging OSINT tools and methodologies, testers can comprehensively enumerate the organisation’s digital footprint, laying the groundwork for a comprehensive assessment.
2. Mapping of Attack Surface
Once assets are identified, penetration testers utilise OSINT to map out the attack surface – the points of entry or vulnerabilities that could be exploited by malicious actors. This involves gathering intelligence on software versions, open ports, and potentially misconfigured services. By analysing publicly available information from sources such as social media, forums, and online repositories, testers gain a comprehensive picture of the organisation’s external infrastructure from an attacker’s perspective, allowing them to tailor their attack strategies accordingly.
3. Discover Unhygienic Practices
Through OSINT, testers can uncover information about internal processes and security practices that require improvement, such as leaked credentials and risky information-sharing practices. Analysing publicly available information about employee activities during a penetration test, such as social media posts or leaked credentials, allows testers to simulate real-world attack scenarios.
This deeper understanding allows testers to leave no stone unturned, exploring multiple attack paths leading to the compromise of the external perimeter. The result is a more thorough penetration test, uncovering vulnerabilities that could otherwise remain hidden.
You may also be interested in: External Perimeter Penetration Testing | Examining Threats Targeting Your Business’ External Perimeter
The Practical Value of EPPT: Bridging the Gap to Red Teaming
Evolution of Network/Infrastructure Testing
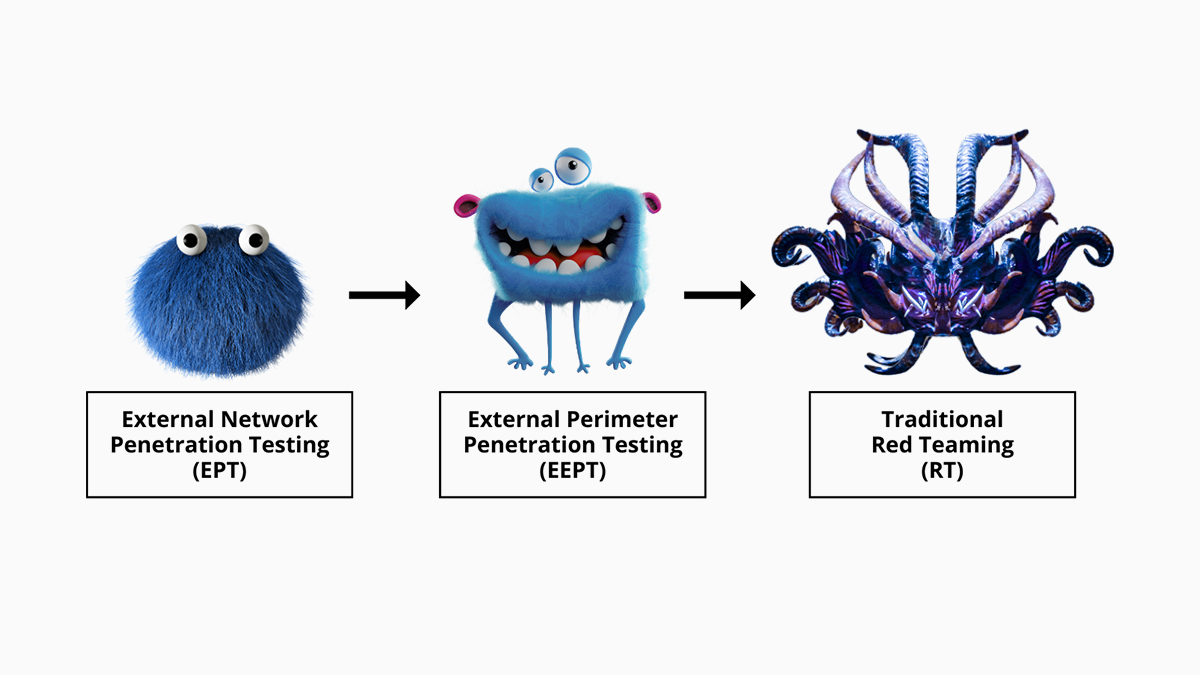
Imagine you’ve conducted a traditional External Network Penetration Test to strengthen your internal patch management processes. You seek to further refine your security posture, but Red Teaming, with its complexity, seems out of reach at present.
Here’s where External Perimeter Penetration Testing (EEPT) comes through. Its open-scoped nature serves as a stepping stone for Red Teaming, bridging the gap between traditional assessments and full-blown simulated attacks.
While there is a visible trend of Red Teaming exercises shifting to an Assumed Breach approach, not all threats originate from insiders. External Perimeter Penetration Testing serves a critical role in clearing the low-hanging fruit on your external perimeter, before eventually transitioning into a Red Teaming’s assumed breach scenario.
If you are seeking to enhance your cybersecurity posture, look no further than Privasec. As a leading provider of cybersecurity solutions in Singapore, including penetration tests, we offer tailored assessments designed to identify and mitigate risks across all facets of your organisation’s digital infrastructure.






















