Evolution of Perimeter Security
For years, cybersecurity professionals have relied on the concept of “perimeter” to protect their organisations. This perimeter was typically a physical barrier, like a firewall, that kept attackers out of the network. Imagine a medieval castle. The castle walls were the perimeter, and they kept attackers out. Inside the walls, the people inside the castle were safe. This is how traditional cybersecurity worked. The firewall was the castle wall, and it kept attackers out of the network.
In the digital age, the perimeter has become increasingly porous. Organisations no longer have a single, well-defined perimeter as they leave a vast online presence, including social media accounts, cloud storage, and public records. This means that attackers can find information about an organisation from many sources, and they can use this information to launch attacks.
While the downside of this is that the open nature of digital footprint means it is widely available to motivated attackers; the good news is that there are steps that organisations can take to protect themselves in the new reality. One important step is to use Open-Source Intelligence (OSINT) to gather information about themselves and identify potential vulnerabilities. OSINT can help organisations to understand their true perimeter and take steps to protect themselves.
Existential Threat Against the External Perimeter
The digital age has expanded the attack surface for organisations. The technology stack is no longer the only place where damage can be inflicted on enterprises’ assets, brand, and reputation. The new perimeter is now considered the sum of all publicly facing systems plus all the information available about the organisation that could be used against it, whether directly or indirectly.
Blind spots on the perimeter start to form as modern-day organisation introduces more productivity workflows, such as:
- Hybrid infrastructure (e.g. Microsoft Exchange) consisting of a mixture of on-premises and cloud facilities.
- Cloud-based blob storage such as S3 and GCP buckets.
- SaaS platforms like CRM, ZenDesk and Slack.
- BYOD (Bring Your Own Device) policy in the workplace.
User behavior and unhygienic practices also add fuel to the fire, causing the bypass of perimeter defenses to be much easier. Corporate account misuse, insecure information sharing via third-party cloud storage provider, and poor security habits – these seemingly minor actions can have disastrous consequences. Whether done maliciously or inadvertently, these decisions prevent organisations from gaining any visibility over that data being transferred across the globe.
Other common breaches of day-to-day OPSEC also includes:
- Exposing the design employee ID badges on social media.
- Uploading a photo of selfie without censoring background information displayed on a monitor.
- Leaving sensitive information unattended.
- Not locking laptops before leaving the workstation.
The Iterative Lifecycle of External Perimeter Penetration Testing
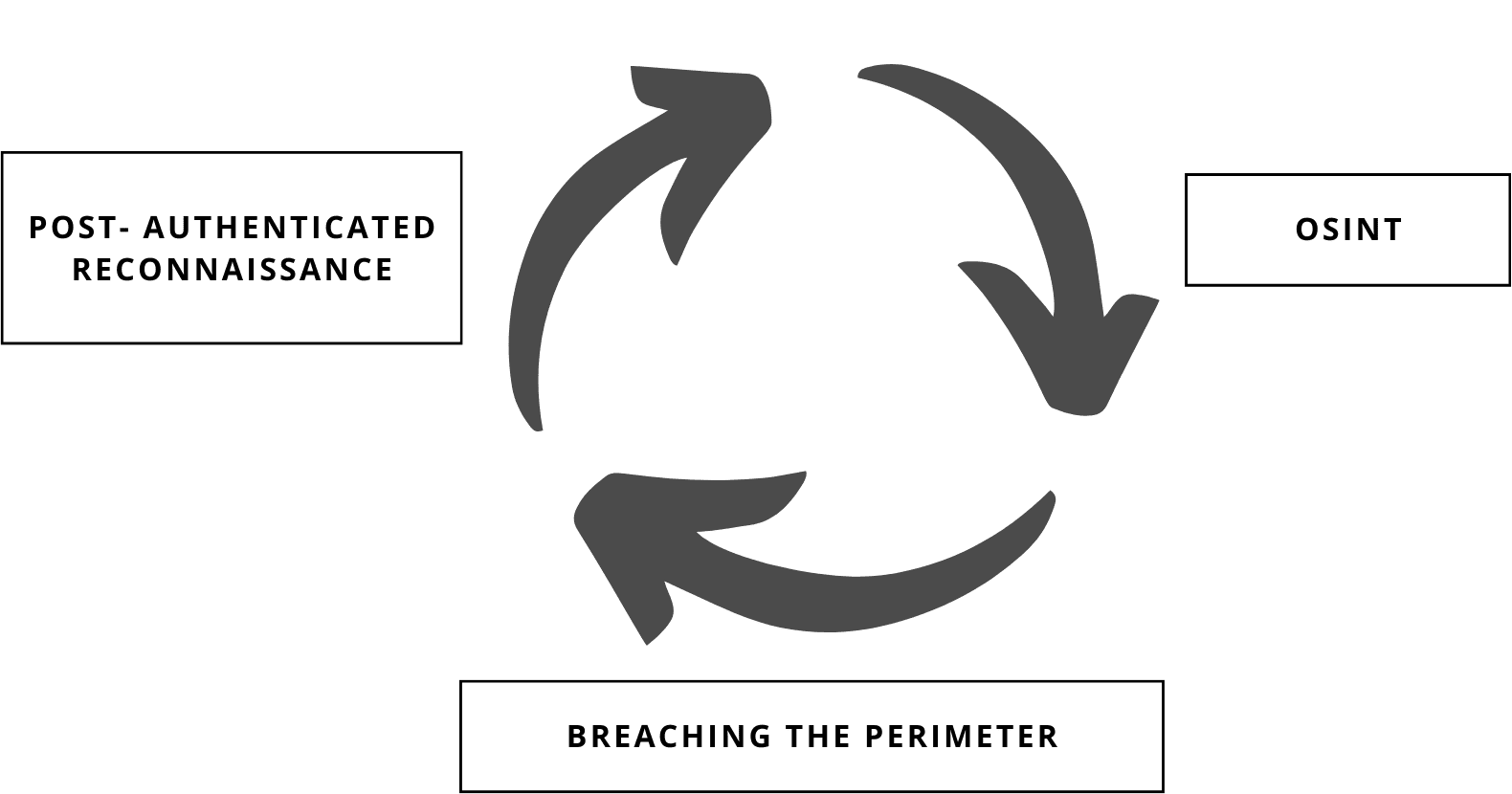
An External Perimeter Penetration Test (EPPT) doesn’t follow a linear path; It starts with a single thread – the provided domain name. From there, OSINT creates a snowball effect. Each discovery opens doors to further exploration and adds another layer to the understanding of the organisation’s external perimeter and potential attack paths.
Once armed with a comprehensive understanding of the attack surface, the lifecycle transitions to breaching the perimeter. This stage involves connecting the dots to understand how they can be exploited in sequence, and how a seemingly minor weakness could lead to a larger compromise. However, unlike traditional penetration testing, the emphasis here is on breadth, not depth. The objective is to unlock as many unique entry points as possible, rather than delve deep into any specific system.
After successfully breaching the perimeter, the focus shifts to gathering information within the network. This stage involves employing various techniques such as mailbox pillaging to gather internal intelligence. However, it’s important to remember that this stage typically doesn’t involve extensive lateral movement or privilege escalation. The goal is to gain enough understanding on how information originated within the internal network can be applied externally.
The final report is accompanied by a comprehensive OSINT report. We don’t just list vulnerabilities; we tell a story – a narrative of how an attacker could exploit them, the potential consequences, and most importantly, actionable steps for remediation. While not all OSINT findings translate to immediate threats, they offer valuable foresight. We include them in our report to equip you with a comprehensive understanding of your potential attack surface, even for vulnerabilities that haven’t fully materialised yet. This proactive approach empowers you to stay ahead of evolving threats.
Conclusion
In today’s interconnected world, security is not just about fortifying the castle walls. It’s about understanding the invisible landscape that surrounds them. With External Perimeter Penetration Testing (EPPT), organisations can gain a deeper understanding of their external attack surface and take proactive steps to secure their ever-expanding digital footprint. Remember, true security lies not just in building walls, but in actively exploring the unknown and preparing for the unexpected.
The EPPT lifecycle is not a singular event, but a continuous loop of discovery and improvement. By regularly conducting these assessments and incorporating the learnings, organisations can proactively identify and address gaps in their external perimeter, ensuring that it remains a robust barrier against ever-evolving threats.