Offensive security plays a crucial role in strengthening an organisation’s defences by proactively identifying and remediating vulnerabilities before they can be exploited by malicious actors. Approaching offensive security pre-emptively establishes a powerful strategy to stay in the vanguard against potential cyber threats.
In this blog post, we will delve into the concept of offensive security, encompassing exploring its advantages, dispelling common misconceptions and providing guidance on selecting the appropriate offensive cyber security solutions in Singapore for your business.
In addition, we will be discussing the seamless integration of Offensive Security and Governance, Risk, and Compliance (GRC) services to bolster your organisation’s cyber resilience and reduce cyber risks.
What is Offensive Security?
Offensive Security, often referred to as penetration testing or ethical hacking, entails authorised experts replicating real-world attacks to unveil vulnerabilities in an organisation’s networks and applications. Through these simulated attacks and the subsequent assessment findings, offensive security specialists offer actionable recommendations, insights, and guidance, contributing to the enhancement of an organisation’s cyber resilience.
Proactive offensive security provides numerous advantages to organisations. For instance, a penetration test facilitates the early discovery of vulnerabilities, thereby enabling swift remediation to address the weaknesses before they become exploitable. In addition, it aids organisations in meeting regulatory requirements and upholding industry standards.
Ultimately, this proactive and cost-efficient offensive security approach empowers organisations to sustain a competitive advantage in an ever-changing threat environment.
Types of Offensive Security Services
| Types of Offensive Security Services | Process | Benefits |
| Vulnerability Assessment and Penetration Testing (VAPT) | ➤ Involves identification of vulnerabilities through the realistic simulation of a cyber-attack. ➤ VAPT could potentially be performed on the following modules: • Internal and External Network • Web Application and API • Mobile Application • Cloud • Wireless Systems • IoT Devices | ■ Identifies vulnerabilities across various systems and networks. ■ Helps qualify and quantify risks, enabling the prioritisation of remediation efforts. ■ Enhances overall security posture. ■ Provides insights for improving security controls and configurations. |
| Red Teaming | ➤ Involves striking an effective balance in assessing the People, Processes and Technology of an organisation. | ■ Broader scope, able to potentially identify findings across the PPT framework that would not usually be caught in a traditional penetration test. ■ Most realistic form of testing for an organisation. |
| Social Engineering and Phishing | ➤ Involves directing focus towards the organisation’s most vulnerable point in defence, which lies in the human factor. | ■ Highlights the importance of security awareness and training. ■ Identifies potential weaknesses in policies and procedures. ■ Helps educate employees about common social engineering tactics and how to prevent falling victim. |
Cloud Security Assessments Learn more: Cloud Security — Getting Ready For The Cloudy Days | ➤ Involves evaluation of an organisation’s Cloud Security Posture using industry best practices and best-of-breed assessment technology across various platforms. | ■ Identifies security gaps specific to cloud environments. ■ Helps ensure compliance with cloud security best practices. ■ Assists in securing cloud infrastructure and data from unauthorised access or breaches. |
Tabletop Exercises Learn more: A Recipe For Success: The Key Ingredients For A Successful Tabletop Exercise | ➤ Involves tailored scenarios crafted towards simulating real-world cyber incidents to test the effectiveness of incident response plans and procedures. | ■ Assess the incident response plan and obtain critical insights. ■ Bolster crisis management for business continuity while enhancing cross-department communication and collaboration. ■ Demonstrate robust security posture and meet compliance requirements. |
Common Misconceptions About Offensive Security
| Myth | Truth |
| Myth #1: Offensive Security Is Malicious | Offensive security is often misunderstood as engaging in malicious activities. However, it is important to clarify that offensive security is a legitimate and ethical practice that requires explicit authorisation from the organisation being tested. Security professionals involved in offensive security act in the best interest of the organisation, aiming to identify and address vulnerabilities effectively. |
| Myth #2: Offensive Security Is Unnecessary with Strong Defences | Some organisations hold the mistaken belief that robust defensive cyber security solutions alone can adequately safeguard their systems. However, it is crucial to look at offensive security as a complementary strategy to proactively reveal overlooked vulnerabilities that may escape detection by defensive measures alone. It offers a holistic perspective of an organisation’s security stance and effectively reinforces its defences. |
| Myth #3: Automated Scanners Can Replace Offensive Security | While automated scanning tools have their benefits, it is important to recognise their limitations. They cannot fully replace the human intuition and creativity essential in offensive security practices. Automated tools may encounter difficulties in identifying complex vulnerabilities, leading to false positives or missed critical issues. Skilled offensive security professionals provide in-depth analysis and tailored recommendations that surpass automated scanners’ capabilities. |
| Myth #4: Offensive Security Is Expensive | Despite the misconception that offensive security is costly, it is important to consider the statistics. In 2022, the average total cost of a data breach amounted to USD 4.34 million. In contrast, the investment in offensive security assessments as well as cyber security solutions is relatively modest, leading to overall cost savings for organisations in the long run by preventing potential ransomware incidents and reducing the impact of security breaches. |
Tips For Choosing the Right Offensive Security Services
To help organisations make well-informed decisions when selecting the right offensive security services that align with their specific needs, it is advisable to consider these tips:
Tip #1: Consider Your Goals
Always keep in mind your objectives, whether it is vulnerability detection, compliance assurance, incident response improvement, or a combination of these factors. Maintaining a clear goal in mind will guide you in selecting the most suitable offensive security services from the diverse range of options available, including penetration tests and tabletop exercises.
Tip #2: Regulatory Compliance
If your organisation operates in a regulated industry, ensure that your chosen offensive security service aligns with the necessary compliance requirements and relevant frameworks or best practices.
Tip #3: Assess Your Specific Needs
It is crucial to assess your organisation’s specific needs, including the systems, applications, compliance obligations, and industry best practices. This holistic evaluation ensures that the chosen offensive security services are tailored precisely to your unique requirements, thereby maximising the efficacy of your cyber security solutions.
Tip #4: Seek Expertise
Ensure you engage experienced and reputable offensive security service providers who possess the necessary certifications, expertise, and knowledge in your specific areas of focus.
Tip #5: Track Record and Reputation
It is advisable to carry out research on the track record and reputation of your chosen offensive security service provider. This can be achieved by reviewing client testimonials, case studies, and industry recognition.
Integrating Offensive and GRC
To achieve the most optimal security posture, it is recommended to integrate both proactive offensive security and GRC services.
By combining both strategies, organisations can bolster their defences, detect vulnerabilities, and respond effectively to potential threats. This culminates in the establishment of a resilient and comprehensive cybersecurity strategy.
Some of the benefits of integrating both offensive and defensive security are listed below:
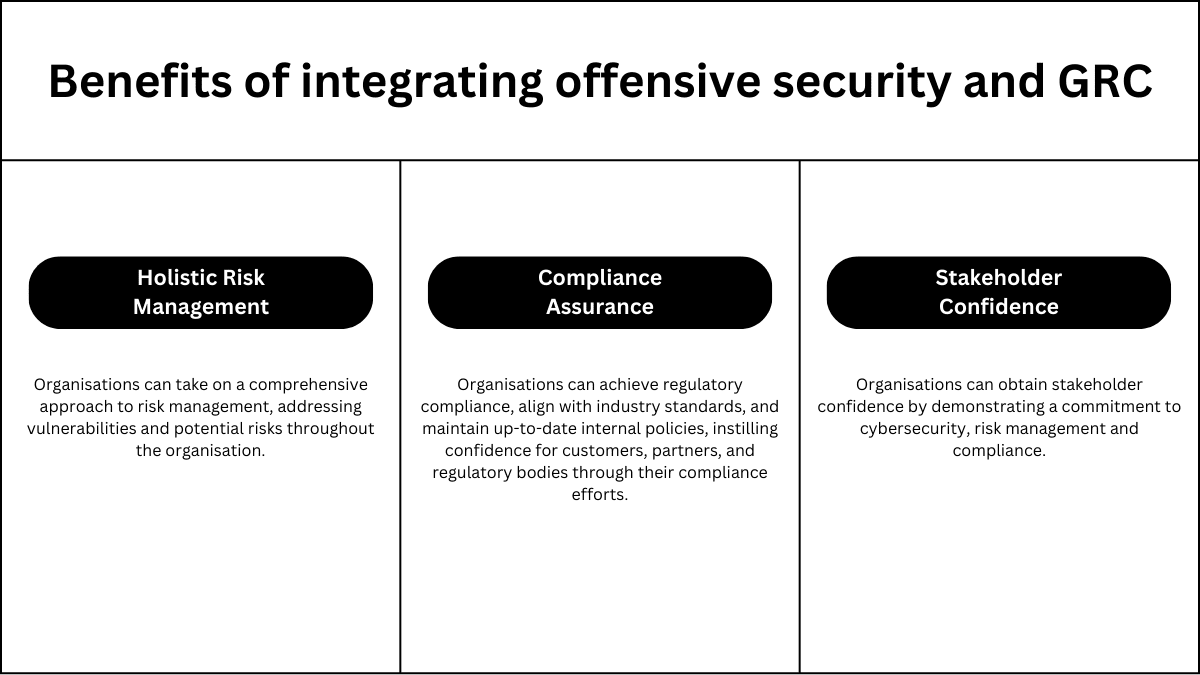
In Summary
Proactive offensive security through penetration tests, tabletop exercises, and more can greatly enhance organisations by facilitating the early detection of vulnerabilities, bolstering security readiness, and ensuring compliance with regulatory requirements. Nonetheless, it is crucial to discern the company’s specific goals and objectives to select the most suitable offensive security services. Organisations should also consider integrating these proactive offensive security services with GRC services to establish a comprehensive security strategy. This will ultimately result in a stronger security stance and heightened confidence among stakeholders, customers, and partners.
Ready to take your organisation’s offensive security strategy to the next level? Get in touch with our team at Privasec today.