The concept of Red Teaming has been floating around. But what exactly is red teaming?
Red Teaming is a concept that originates from the US military, which aims to simulate and demonstrate attacks of real-world adversaries, with the attempt to compromise the various aspects of security.
While the military focuses on simulating war attacks, in the InfoSec World, a Red Teaming engagement focuses on testing and assessing the various aspects of an organisation’s overall security. This includes:

- Physical aspect – Locks and the physical doors and barriers of your premises, etc.
Some examples would be lockpicking or Radio Frequency Identification (RFID) skimming.
- Social aspect – Your employees, etc.
In terms of their security awareness and general knowledge of social engineering methods such as phishing, tailgating and impersonation attacks.
- Technological aspect – Routers, devices, Local Area Network (LAN) ports etc.
Some examples would be accessing sensitive information by connecting to your LAN ports or even breaching the internal WIFI access. But don’t mistake it for your usual network infrastructure penetration test.
1. Engagement Objectives
The first difference would be that a Red Teaming engagement is objective-focused – on crown jewels, whereas a Penetration Test focuses on identifying as many security gaps/vulnerabilities within the given environment.
Also, Red Teaming focuses on achieving a particular set of outcomes, while the penetration test aims to achieve a wide breadth.
Some examples of Red Teaming include:
– Gaining access to your private Wi-Fi in your premises
From a Penetration Test perspective, we would brute force the password or even drop Internet Control Message Protocol (ICMP) packets to gather information and decipher the password.
From a Red Teaming perspective, it can be done through either impersonating as a new employee to ask around for the Wi-Fi password or even impersonating as a service repair man from the internet provider to gain access to the network/ server room.
2. Engagement Objectives
Red Teaming focuses on evading detection and, as such, generally creates little noise within the environment.
In contrast, a traditional penetration test, for example, Network Infrastructure Penetration Test, focuses on identifying all possible vulnerabilities in the environment within the stipulated timeframe. And as such, these engagements typically generate a more considerable amount of traffic and noise within the environment.
However, this would vary from project to setup. For example, there might come a need to bypass endpoint detection within an internal environment for a network infrastructure penetration test. Hence, lesser noise will be generated during the engagement.
Read more about Red Teaming VS Penetration Testing here
What are the benefits of a Red Team?
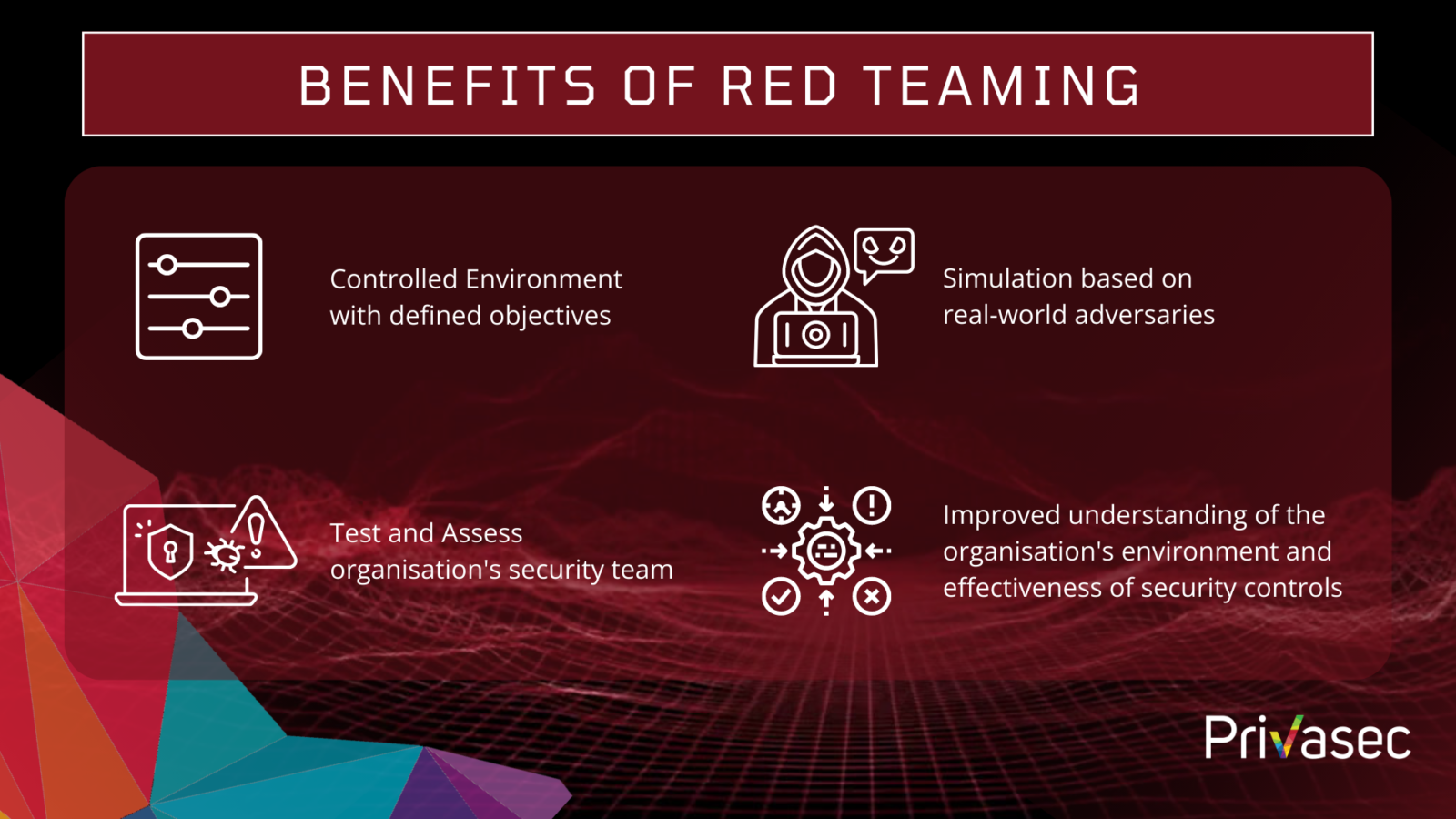
The Red Teaming presents a controlled environment to test and assess an organisation’s security team against a real-life simulated attack. With that, organisations can better understand their environment and fully assess the effectiveness of their security controls.
In the context of Working from home
While the traditional concept of Red Teaming often involves physical break-in to the environment, due to Covid-19 and the ever-changing landscape, there has been a shift from the traditional lock breaking to the perspective of social engineering. This includes phishing and pivoting attack vectors. Or rather, the Red Team can combine both, with phishing being the means to the cause of a compromise.
For example, a malicious executable can be attached to an email.
With it being downloaded and run on the staff’s computer, this can be propagated to various other members of the organisation, allowing the attacker to gain access to the internal environment. This is extremely crucial, especially looking at the current climate with employees working remotely and using Virtual Private Network (VPN) to access internal resources.
Therefore, even in the context of remote working, Red Teaming can test your technological controls and ensure that training is in place to prevent a malicious attacker from gaining access to the system.
What are some requirements of a Red Teaming Engagement?
Maintaining a minimum level of security posture.
Conducting regular penetration tests, like Network Infrastructure Penetration Test and Web Application Penetration Test. This weeds out the low-hanging fruits/ vulnerabilities/ security gaps within the environment. This allows the Red Team to focus the engagement on achieving the crown objectives.
Possess a certain level of cyber security maturity in the form of policies.
Having relevant policies, processes and plans like Incidence Response Plan (IRP), Business Continuity Plan (BCP), and Disaster Recovery Plan (DRP) in place. This ensures that employees can respond in the event of an attack and assess the responses during the engagement.
All in all, a certain level of the organisation’s cyber maturity is required for an effective Red Teaming engagement as the Red Team enters the environment.

























