Many organisations don’t fully understand the difference between vulnerability scanning, a penetration test, and Red Teaming.
We previously discussed the difference between a vulnerability scan and a penetration test. Read about it here.
In this article, we explain the difference between a red team assessment and a penetration test in Singapore and which assessment is best suited for your organisation.
What Is a Red Team Assessment?
It is an objective-driven attack simulation offering a realistic assessment of the resilience of your IT controls, such as firewalls, and evaluating the overall security posture of the organisation. This simulation scrutinises the effectiveness of the people, processes, and technology in identifying, mitigating, and responding to authentic and targeted cyber threats.
Red Team attack simulations go beyond testing an organisation’s IT controls (i.e. firewalls), involving its people, processes and facilities. However, it is not for everyone and is usually performed by organisations with mature security programmes (i.e. positive penetration test results, controls to detect security events, and a security-aware culture).
What Is a Penetration Test?
A penetration test is a simulated cyberattack conducted on a computer system, network, application, or organisation to identify vulnerabilities and weaknesses that malicious hackers could exploit. The primary objective of a penetration test is to assess the security of the system and provide insights into how to strengthen defences.
It is more suited for organisations that are still in the early stages of their security programmes and are looking to identify insecure business processes, poor security settings, or other weaknesses that a hacker could easily exploit.
Choosing Between a Red Team Assessment and Penetration Test
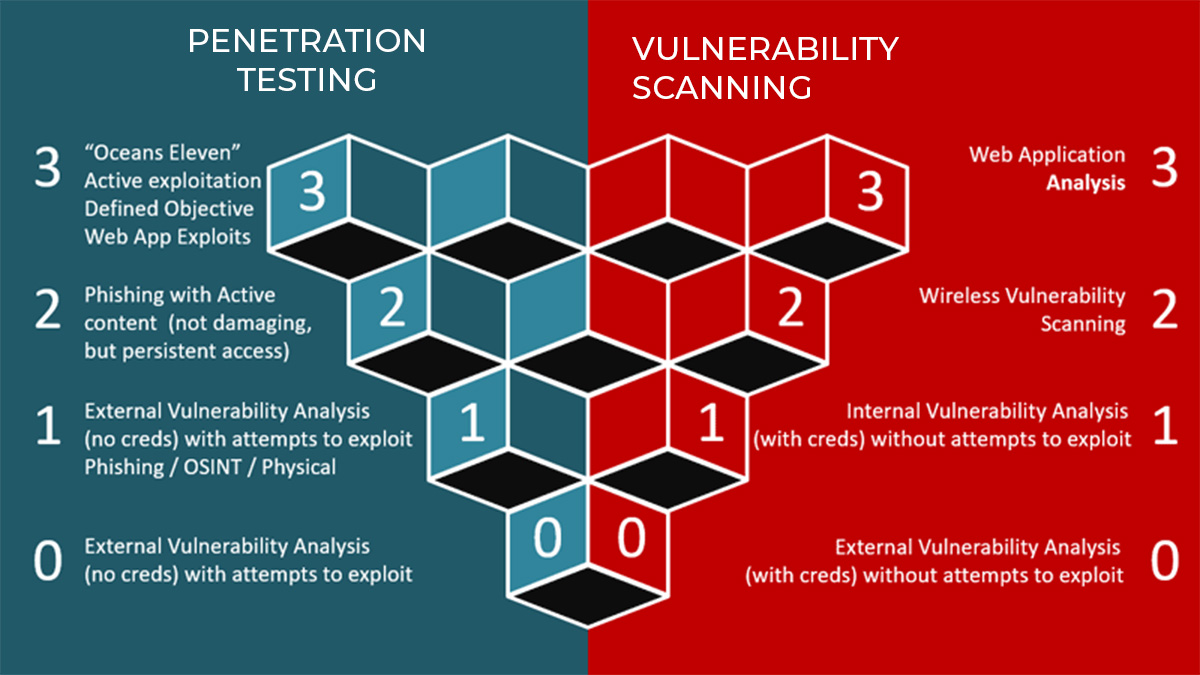
There are several other factors to consider before choosing one. Some of these include:
1. Aim
The goal of a penetration test is to find, exploit and thus determine the risk of architecture vulnerabilities. A Red Team assessment, on the other hand, is more targeted and the goal is to test the organisation’s detection and response capabilities. As opposed to a penetration test, a Red Team attack is multi-layered and focuses on the objectives of an attack rather than on the methods utilised.
2. Methodology
Some of the best industry penetration testing methodologies include: The Penetration Testing Execution Standard (PTES), Open Web Application Security Project (OWASP) Testing Guide, NIST SP 800-115 Technical Guide to Information Security Testing and Assessment. Red Team assessment combines intelligence gathering, social engineering, hacking, physical intrusion and other deceptive techniques to compromise defences and gain access to critical information.
3. Scope
The Red Team assessments are more targeted than a penetration test. Its scope defines the don’ts (what cannot be done) rather than the do’s and thus replicates a real-life, determined attacker. The scope of a penetration test is generally determined by a finite asset (i.e. web-application) that is being tested.
4. Effort and Duration
Since Red Team engagements involve more stakeholders, it usually takes 3-4 weeks, or even months, to complete. On the other hand, a penetration test often takes 1-2 weeks.
Selecting between red team assessments and penetration tests requires a tailored approach, acknowledging the uniqueness of each organisation. To make an informed decision, it is crucial to carefully assess your organisation’s specific needs and its existing security landscape.
Privasec’s Red Teaming Services
Our red team assessments provide a more realistic way to test the resilience of not only your IT controls (i.e. firewalls) but also of your people, your processes and your facilities. Through meticulously simulated attacks, genuine vulnerabilities in your security framework are exposed, demanding immediate remediation. The scope of a RED Team engagement primarily delineates what cannot be done, mirroring the unrestrained approach of a real-life attacker rather than specifying explicit actions.
Privasec’s Penetration Testing Services
Privasec RED consultants use thorough and proven Penetration Testing and Vulnerability Management methodologies that comply with, or exceed, industry best practices to identify and improve your organisation’s security architecture. They include but are not limited to Web Application Penetration Testing, External Penetration Testing, Internal Penetration Testing, Cloud Penetration Testing, Mobile Application Penetration Testing, Remote Access Penetration Testing, OWASP Top 10 Penetration Testing, Wireless and RFID Penetration Testing, Social Engineering and Physical Security Penetration Testing.
Read more about our penetration testing services here.
Let us help you enhance your organisation’s security posture with our cyber security solutions today – get in touch with our team at Privasec.






















