In the ever-evolving landscape of cybersecurity, staying one step ahead of potential threats is paramount for businesses. Penetration testing stands as a robust strategy to fortify digital defences, safeguard sensitive information, and ensure the resilience of an organisation’s systems. As companies in Singapore and beyond seek to bolster their security measures, the importance of conducting a penetration test has become increasingly pivotal.
Keep reading to delve into the depths of penetration testing, exploring what it entails and the various methodologies.
What Is Penetration Testing?
At its core, a penetration test embodies a controlled yet realistic attempt to breach the security barriers of a system, network, or application. Certified ethical hackers take centre stage, meticulously scrutinising potential vulnerabilities that could be exploited. These assessments encompass both manual and automated techniques, targeting a wide array of organisational resources, from mobile and web applications to APIs and Active Directory systems.
The ultimate aim is to unearth misconfigurations or security loopholes that could potentially grant unauthorised access to sensitive resources. The vulnerabilities are then ranked based on the perceived risks, likelihood and impact.

Penetration Test Types
Black Box
Imagine a scenario where the tester steps into the shoes of an offshore attacker, armed with minimal to no prior knowledge of the target. This type of testing mirrors real-life attack scenarios from external sources. Although it provides an authentic perspective, it is crucial to note that the tester’s time may not be fully optimised, potentially overlooking vulnerabilities within internal systems. Despite its limitations, black box penetration testing is invaluable in revealing external-facing weaknesses.
White Box
In stark contrast, white box penetration testing equips the tester with a wealth of initial knowledge about the environment. This insight could stem from privileged account access, source code analysis, or comprehensive architectural documentation. Armed with this knowledge, testers can dissect the inner workings of the target, scrutinising potential points of vulnerability from both internal and external standpoints. White box testing provides a holistic assessment with the unique advantage of allowing organisations to focus their penetration tests on the crown jewels or specified scope. This ensures a thorough assessment that aligns precisely with their critical assets and security priorities.
Grey Box
Blending the best of both worlds, grey box penetration testing strikes a balance between the unknown and the known. Testers possess partial insights into the target, offering a pragmatic compromise between effort and comprehensiveness. This approach is efficient and effective , where it ensures that testers are armed with enough information to identify vulnerabilities while still emulating the partial information an attacker might possess.
Navigate Threats With Confidence
As the digital realm continues to expand, the threat landscape grows in complexity. This makes embracing a proactive cybersecurity stance all the more crucial. Conducting a penetration test emerges as a beacon of defence, helping organisations in Singapore and beyond navigate the ever-shifting seas of cyber threats.
By understanding the nuances of black box, white box, and grey box testing, businesses can tailor their security strategies to effectively combat potential risks.
Our team at Privasec is experienced and trained in penetration testing. We also offer a range of cybersecurity products that will help businesses safeguard their data.
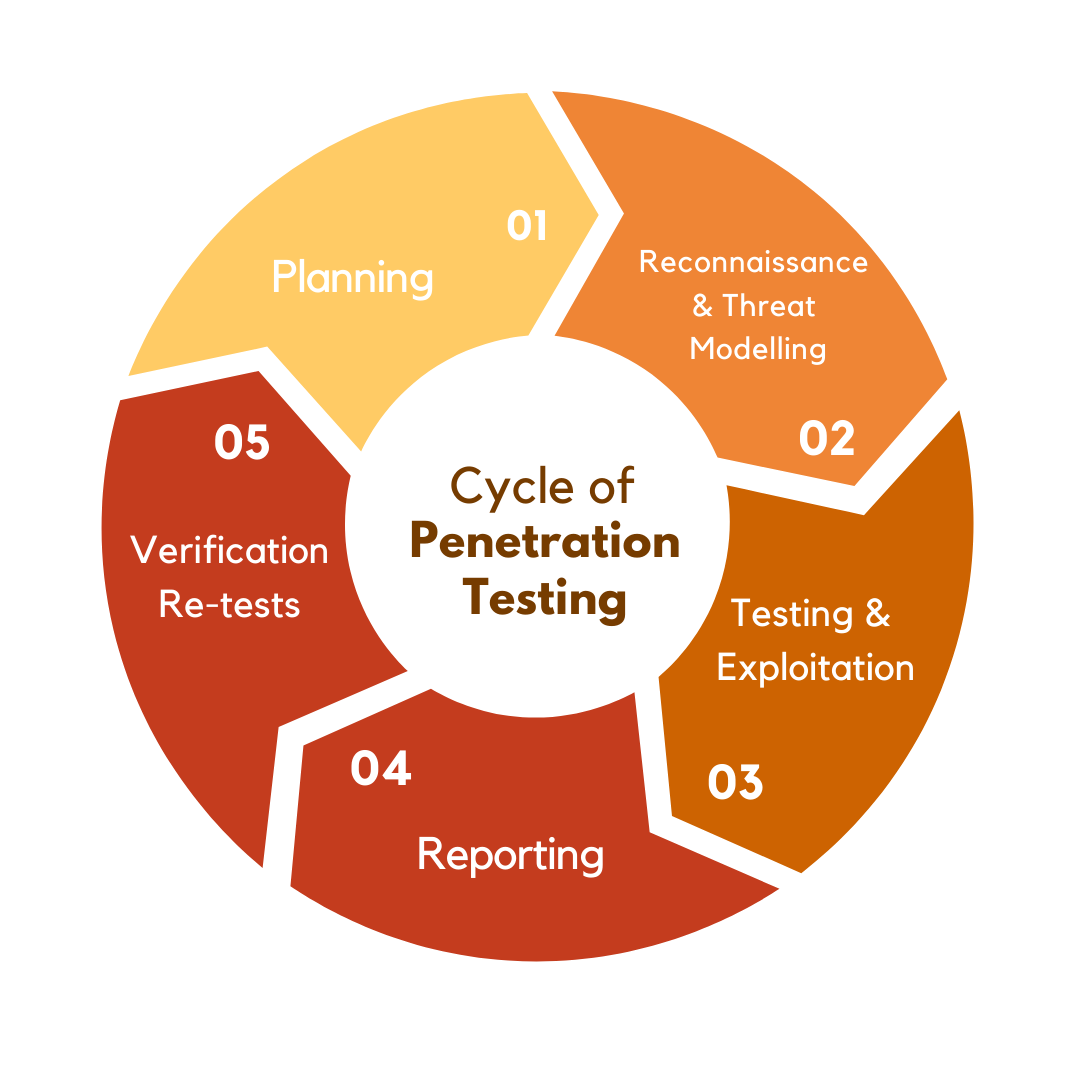
Here Is A General Outline Of A Penetration Test
1. Planning And Reconnaissance
An initial meeting to understand your needs in terms of penetration testing objectives/goals and to discuss the right level of testing (white, gray, black box) for your organisation. This will determine the scope of the test, logistical requirements such as IP whitelisting, user accounts, Architecture Design documents and to address any limitations such as time frame or Rules of Engagement.
2. Threat Modelling
Upon completion of the Rules of Engagement (ROE) document, Privasec will perform a technical validation of the scope and environment that comprised of the target area for the review.
This is to gain information about the possible attack vectors for threat modelling. where the assets and processes that could be targeted by attack and the potential impact on the company.
3. Exploitation and Testing
Privasec will conduct the actual manual exploitation of the attack vectors identified earlier and via the course of assessing the target area in scope. This is to determine the exploitability and extent of damage of which an attacker can cause from the exploitation of the attack vectors.
The exercise will be conducted in accordance with Privasec’s Penetration Testing methodology, which references multiple industry recognised frameworks (i.e OWASP Top 10, NIST and etc) and the extent of exploitation will be based on the ROE discussed earlier.
An example of vulnerability according to OWASP Top 10 is a successful exploit on broken authentication. This would allow an attacker to compromise admin level credentials and make changes to the system therefore compromising the Confidentiality, Integrity and Availability (CIA) of the system
4. Reporting
A practical report that details and prioritise the identified vulnerabilities along with its impact and remediation guidance is drafted and discussed with the client. This is to ensure that all false positives are removed, and risk ratings provided are appropriate taking into considerations the business need and existing controls.
5. Verification Re-Tests To Ensure Your Fixes Have been Implemented Correctly
One round of retest will be performed once after appropriate risk management is done on the findings raised in draft report. If this is not required, the report will be released as “final”. The final report will be issued with updates on the retested findings.