In today’s rapidly evolving digital landscape, the continuous advancement of technology has introduced new cybersecurity norms and challenges. As organisations embrace hybrid and cloud-based infrastructures to fuel their growth and innovation, ensuring robust security measures through the right cybersecurity solutions and conducting regular cloud security assessments becomes an increasingly critical task.
Learn more: When working from home isn’t as safe
Tailored to the unique needs of each organisation, the design and establishment of IT systems and infrastructure hinge on how people interact with these resources. This shapes the core of how these resources support business functions and processes. Identity Management, emerges as the cornerstone of secure business operations, forming a fundamental pillar of a comprehensive cybersecurity strategy to safeguard sensitive data and resources.
In this blog post, we will delve into the different aspects of Identity Management and how it forms the foundation of secure business operations.
What Is Identity Management?
Identity Management ensures secure and appropriate access to an organisation’s critical systems and data. With effective management of digital identities, organisations can control who has access to their resource, when they have access and what they can do with the access.
Managing users’ and devices’ identities, access rights, and any modern workplace environment can be challenging. The use of:
- distributed systems, and cloud-based applications and services;
- support for a distributed workforce, such as remote workers, third-party vendors and contractors;
- the varied devices used, such as BYOD mobile devices; and
- the need to comply with evolving regulations and policies.
has brought the concepts of Identity Governance and Administration (IGA), Identity and Access Management (IAM) and Privileged Access Management (PAM) to the forefront. These areas, while overlapping, focus on different aspects of identity management.
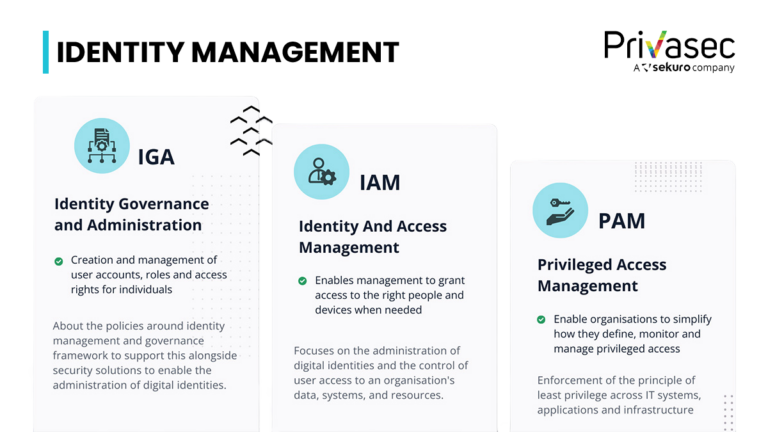
Comparing the two, IAM can be seen as a part of IGA, where the aspects of governance and consideration of standards and compliance requirements help to ensure IAM policies are aligned and enforced. Privileged Access Management (PAM) focuses on managing privileged accounts, which hold more significant risks due to their level of access. Of the three, PAM is the most narrowly defined.
Key Considerations to Adopt the Right Solution
According to Gartner’s description of IGA, a comprehensive IGA suite must encompass essential capabilities to fulfil the requirements of a typical organisation. These are the key features that are crucial to consider when evaluating an IGA solution’s capabilities.
1. Identity Lifecycle Management
This involves the management of digital identities from creation to deletion. An effective IGA solution should be able to automate the process of creating, updating, and deleting user accounts, thereby reducing the risk of human error and ensuring that access rights are always up-to-date.
2. Entitlement Management
This refers to the management of user access rights or entitlements. The IGA solution should provide a centralised system for managing entitlements, making enforcing access policies easier and ensuring that users only have access to the resources they need.
3. Support for Access Request
The IGA solution should support a streamlined and efficient process for users to request access to resources. This includes features like self-service portals and automated approval workflows.
4. Workflow Orchestration
This involves automating and coordinating complex processes involving multiple systems and stakeholders. The IGA solution should be able to orchestrate workflows for processes like access requests, access reviews, and password resets.
5. Access Certification (Also Called “Attestation”)
This is the process of verifying that users’ access rights are still appropriate and necessary. The IGA solution should support regular access certifications, allowing organisations to demonstrate compliance with various regulations and standards.
6. Provisioning via Automated Connectors and Service Tickets
The IGA solution should be able to automatically provision and de-provision access rights using connectors to various systems. It should also support the creation of service tickets for manual provisioning tasks.
7. Analytics and Reporting
The IGA solution should provide robust analytics and reporting capabilities. This can help organisations identify trends, spot potential security risks, and demonstrate compliance with various regulations and standards. Such data will come in handy during a cloud security assessment — organisations can analyse trends and patterns in user access, permissions, and authentication across cloud platforms for a holistic view of potential risks and areas for improvement.
In addition, a robust IAM system provides organisations with valuable insights into user behaviour, empowering them to proactively identify potential security risks before they escalate into serious threats. By monitoring and analysing user actions, IAM enables swift action against suspicious activities, strengthening an organisation’s security posture. Moreover, these systems help organisations adhere to regulatory requirements, avoiding potential legal and reputational consequences.
This is reflected in numerous industry guidelines and internal standards, such as the Monetary Authority of Singapore’s Technology Risk Management (MAS TRM) Guidelines, ISO 27001 Annex A Controls, NIST CSF and SOC 2 TSC.
Conclusion
In summary, integrating an Identity Governance and Administration (IGA) solution into an organisation’s overall cybersecurity architecture is a strategic decision that can significantly enhance security posture and compliance. IGAs reduce the risk of unauthorised access and potential data breaches and provide a comprehensive view of who has access to what, when, and why, enabling organisations to maintain control over their digital environments.
The successful integration of IGA into a cybersecurity strategy can provide a robust foundation for managing digital identities, enforcing access policies, and maintaining regulatory compliance.
By leveraging Privasec’s cybersecurity solutions in tandem with IGA, you not only fortify your identity management but also establish a comprehensive defence against evolving cyber threats.
Get in touch to find out more about our products and solutions here.
Author: Lim Quan Heng, Regional Head Of Asia
Lim Quan Heng is passionate about making and breaking things, and is driven to solve hard problems. As an entrepreneur active in the field of cyber security, he enjoys tinkering with electronics and writing code. He loves sharing the importance of cyber security with businesses, and helps in aligning it to their business strategies.

























