This blog post unpacks key insights from Privasec’s webinar, “Beyond the Firewall: Mastering External Perimeter Penetration Testing”. With the evolving threat landscape, organisations cannot afford to rely solely on traditional security measures. While internal penetration testing remains crucial, it is vital to extend your security gaze outwards, towards the often-neglected external perimeter.
Traditional Pen Testing vs. Red Teaming
Penetration testing, a well-established security practice, involves simulating cyberattacks to identify vulnerabilities within an organisation’s network. However, it often operates within a defined scope, focusing on specific systems or applications.
Red Teaming, on the other hand, takes a more comprehensive approach. It simulates a real-world attack scenario, assuming an attacker has already infiltrated the system through an assumed breach scenario. Red Teamers then move laterally within the network, simulating the tactics of malicious actors to identify potential damage and data exfiltration.
Not Red Teaming Ready? Start with External Perimeter Penetration Testing!
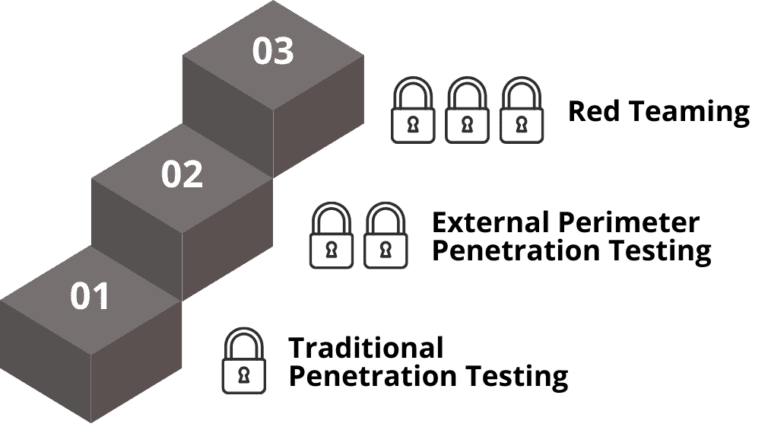
Build your cyber resilience one step at a time. External Perimeter Penetration Testing (EPPT) is a perfect starting point for organisations wanting to go beyond Traditional Penetration Testing. EPPT offers a valuable stepping stone towards red teaming engagements.
EPPT strengthens your external defenses, revealing vulnerabilities attackers might exploit. Once your perimeter is fortified, your organisation be better prepared for a full-scale Red Teaming exercise that simulates a real-world attack, including an assumed breach scenario. This staged approach ensures you get the most value from your security assessments.
External Perimeter Penetration Testing (EPPT)
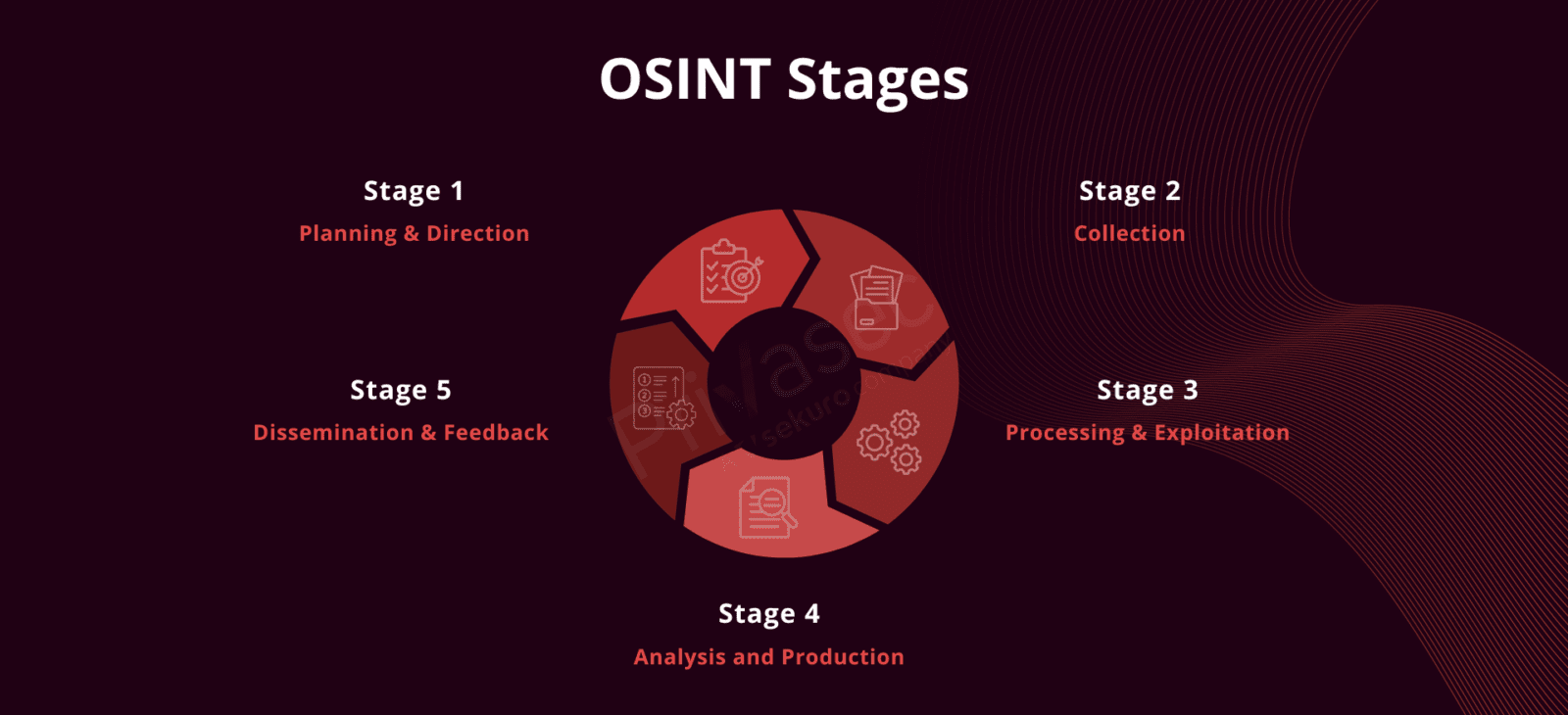
EPPT leverages the power of Open Source Intelligence (OSINT) to conduct a far more realistic penetration test than traditional methods. Pen testers act as malicious actors, employing OSINT techniques to discover publicly available information about your organisation. This could include:
- Leaked credentials from past data breaches
- Risky information sharing practices on social media platforms
- Sensitive data inadvertently exposed in public code repositories
With this intel, pen testers then launch targeted attacks against your external-facing systems, simulating real-world attacker methodologies. This approach provides invaluable insights into your organisation’s true security posture, exposing vulnerabilities that traditional pen testing might miss.
Common Findings from EPPT: What to Be Wary Of

EPPT engagements often uncover a range of concerning vulnerabilities. Here are some of the most common findings:
Exposed Credentials: Leaked credentials from past data breaches are a goldmine for attackers. Hackers can leverage these stolen credentials to gain unauthorised access to your systems.
Risky Information Sharing: Unsuspecting employees might inadvertently share sensitive information on social media or public forums. This information can be used by attackers to target phishing campaigns or craft social engineering attacks.
Unsecured Public Repositories: Sensitive data accidentally committed to public code repositories can be a treasure trove for attackers.
Case Study: When a Telegram Bot Becomes a Weapon
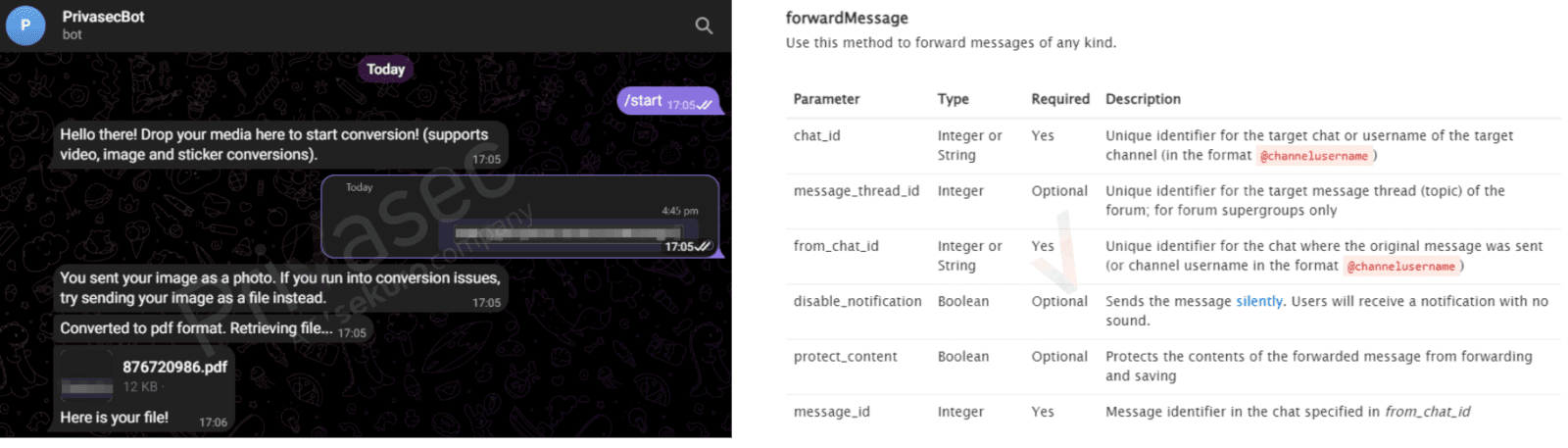
Imagine a seemingly harmless Telegram bot that boosts workflow productivity by allowing users to convert an image snippet into a PDF file with a single button. While this bot’s purpose may seem innocent, it can serve as a gold mine of information for attackers when it’s not implemented securely. An attacker that compromises the Bot’s token could exploit it to sniff on past conversation history between the Bot and other end-users to carve for occurrence of sensitive information. This information can then be used to launch large-scale credential stuffing attacks against other online services.
Keep in Mind
As your organisation scales, managing your internal and external perimeter becomes increasingly complex. Growing organisations face a double-edged sword: expanding attack surface and reduced visibility. Daily digital footprints become harder to control, increasing your cybersecurity risk.
Taking Action: Beyond the Firewall Lies Peace of Mind
The insights gleaned from EPPT are invaluable for organisations looking to strengthen their cybersecurity posture. In today’s digital age, a strong defense starts with a clear understanding of your external perimeters. By incorporating EPPT into your security strategy, you gain a crucial advantage. You can proactively identify and address vulnerabilities before attackers have a chance to exploit them. By proactively fortifying your external defenses, you can achieve true peace of mind and ensure the continued security of your organisation’s data.
We would like to thank all our valued attendees who joined us for our webinar. We look forward to seeing you again in our upcoming events!
Common Questions Asked
To address misinformation while upholding operational security, organisations should verify publicly gathered intelligence through multiple trusted sources and analytical tools. Continuous monitoring and collaboration within established networks are crucial for detecting and mitigating threats posed by misinformation.
Both EPPT and Red Teaming leverage OSINT, but they have distinct purposes and provide different types of value. Here's a breakdown to help you understand the key differences:
Target and Scope:
- EPPT: Focuses on your external perimeter. It simulates real-world attacks originating from outside your network, using OSINT to discover publicly available information that attackers could exploit (e.g., leaked credentials, social media leaks).
- Red Teaming: Takes a broader approach. It simulates a full-blown attack scenario, often assuming an attacker has already infiltrated your network (perhaps through a compromised user account). OSINT helps your organisation understand your security posture, and potential internal vulnerabilities.
Value Proposition:
- EPPT: Helps you identify and address weaknesses in your external defenses before attackers can leverage them. It provides a clear picture of how vulnerable you are to outside threats.
- Red Teaming: Tests your organisation's overall security posture, including your incident response capabilities and internal security controls. It reveals how well you can detect, contain, and recover from a sophisticated attack.
Yes. Red teaming exercises often leverage elevated privileges. Here's how red teaming engagements are conducted with security in mind:
- Pre-defined Scope: Before granting access, a clear scope is established and agreed upon. This outlines which systems and data the red team can target and what actions they're authorised to perform.
- Close Monitoring: Red team activity is closely monitored throughout the engagement. This ensures our exercises stay within the defined scope and don't cause unintended damage.
- Post-Engagement Analysis: After the engagement, a thorough analysis is conducted. This helps identify exploited vulnerabilities and improve your overall security posture.
To safeguard against OSINT techniques, Privasec advises careful sharing and employee education on data privacy. Adjusting privacy settings and scrutinising shared content details, and deprovision inactive accounts are key to preventing leaks and maintaining security.
In a real-world scenarios, attackers might not initially access your network, but potential points like insider threats or compromised devices still exist. Internal network penetration testing simulates breaches past perimeter defenses, exposing vulnerabilities such as weak credentials, mimicking attackers to focus on methods like insider threats and compromised devices.