By Privasec RED Team
Red Team Attack Simulations mimic an adversary attacking your organisation. Red Team Attack Simulations enable you to understand and improve upon your ability to identify and respond to an adversary trying to access your systems or information.
But what actually happens during a Red Team and how does an Attack Simulation work in practise?
Let’s take a look at the 5 steps involved in a successful red team.
Step 1: Confirm Testing Objectives
Red Team Attack Simulations are broad in scope, but focus on specific and targeted objectives based on the more likely and real threats you have to worry about. These objectives drive the Red Team Attack Simulation and are tied to critical business functionality or assets (i.e. ‘crown jewels’).
For example, a financial services institution’s primary security concerns could include the ability for an adversary to perform an unauthorised monetary transaction or to encrypt core business systems as part of a ransomware style attack.
Step 2: Identify Threat Actors
Privasec makes use of Threat Intelligence to identify realistic real world threat actors and to understand and emulate their known methods of attack, thereby creating and executing a realistic simulation.
In our example, Ransomware groups are currently known threat actors targeting financial services institutions.
Step 3: Confirm Attack Approach
Once defined and understood, these testing objectives and threat actors enable Privasec to identify high-level attack scenarios and approaches.
Following our example scenario:
- To simulate a Ransomware style attack, Privasec would attempt to create ‘dummy’ files, then exfiltrate and encrypt those files on a number of selected critical hosts. These actions are intended to simulate the operational approach of a ransomware-style attack without overwriting sensitive files
- To simulate an unauthorised transaction, Privasec would attempt to gain access to financial systems. Access would be demonstrated by submitting a ‘test’ transaction record with specific debug string values that would purposefully not be processed by the automated system
Step 4: Attack Execution
Once the scenarios and realistic attack approach components are agreed upon. Privasec performs the controlled attack execution.
An attack simulation flow for our example could include the following steps:
Reconnaissance
Initial Access
Access Verification
Lateral Movement
Deploy Assets
Remote Access confirmed
Internal Enumeration
Outdated Software
Privilege Escalation
Gather Credentials
Domain Administrative Access
Demonstrate Impact
Understand Processes
Monitor User Sessions
Objective Achieved
Step 5: Attack Reporting
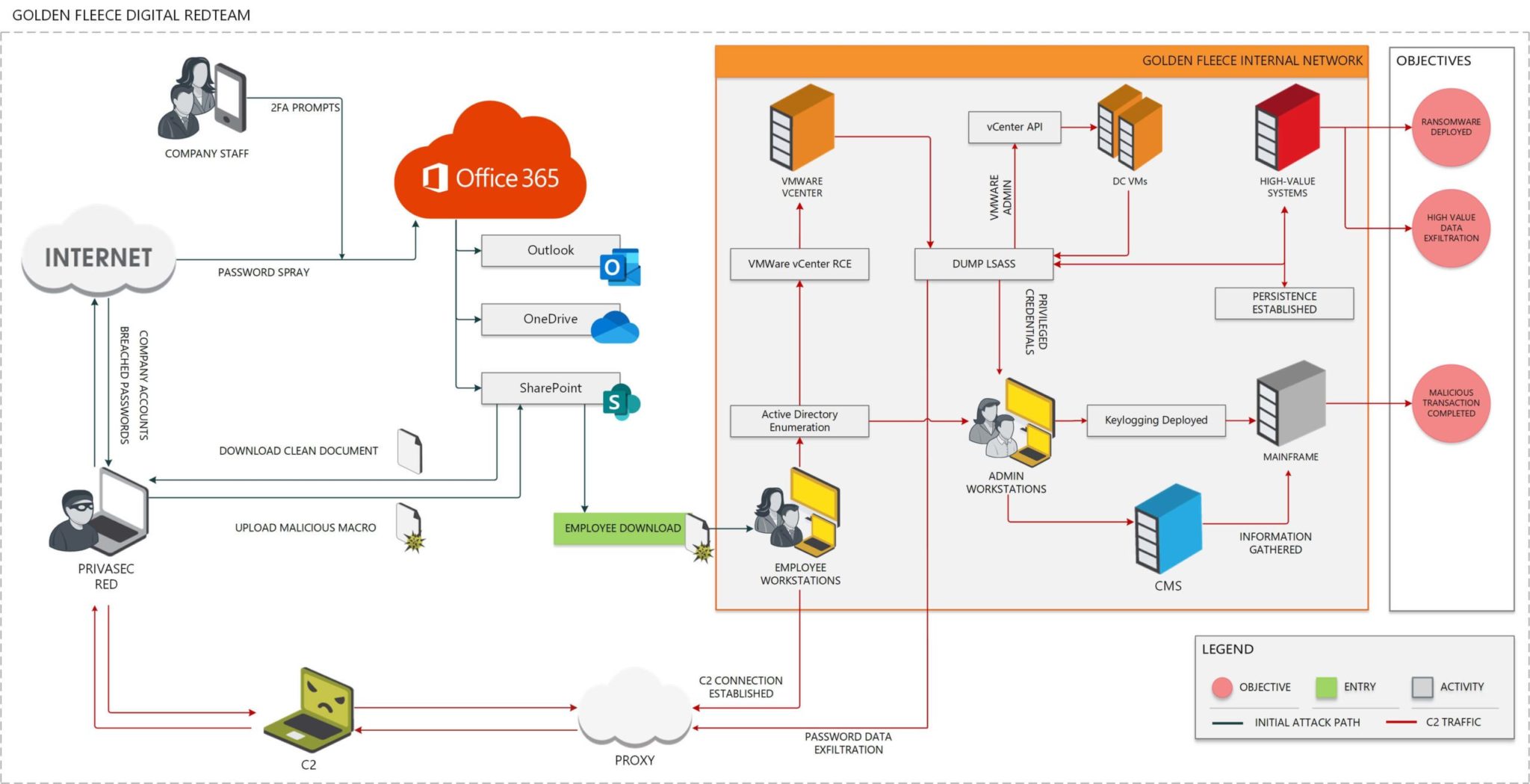
Privasec’s reporting process focuses on the paths and steps taken to reach core objectives (i.e., what we did to get there, how sophisticated our attack was and how accessible it is for a real world threat actor to execute). To enable wider and non-technical understanding and digestion of the root cause, process, and impacts, Privasec creates attack flow timeline diagrams.
In our example, the attack execution described above could be visually represented and understood by the below attack flow diagram:
As business security is also in our DNA, we know that results from a Red Team must be understood at a business level and our executive summary is also crafted with that audience in mind. Privasec identifies and translates the technical impact, to the resulting business risk.