Written by Angela Yuen, Privasec’s GRC and Security Consultant
Introduction
In the cybersecurity landscape today, there are many information security frameworks to help organisations protect their information assets. These frameworks serve as a common language that allows all staff within an organisation, as well as relevant stakeholders to develop a shared understanding of information security risks. It is thus important for organisations to choose the right framework that suit their environment. Broadly speaking, there are three types of information security frameworks:
- Control frameworks which contain a set of baseline control to be implemented.
- Program frameworks which define the requirements for building an effective information security system.
- Risk frameworks which describe the process to manage risks.
ISO 27001 sits within the program framework as it mandates the design and implementation of an Information Security Management System (ISMS). Nonetheless it makes references to the risk management framework to help organisations identify, evaluate, and treat risks surrounding information assets.
What is ISO 27001/ISO 27002?
ISO 27001 is the central framework of the ISO 27000 series and takes a risk-based approach to help organisations manage information security. It provides organisations the requirements for establishing, implementing, maintaining and continually improving an information security management system (ISMS). The core requirements of the standard are supported by a set of security controls, known as Annex A. While organisations are not required to implement all the controls within Annex A, it serves as a catalogue for organisations to select appropriate controls to tackle the information security risks identified, based on business objectives and risk assessment.
ISO 27001 has become the go-to standard for information security as it can be adopted by any organisations regardless of size and sectors who are keen to establish and maintain a working ISMS. There has been increasing pressure, by regulators, clients and other stakeholders, for organisations to proof the robustness of their security controls. Conforming to an international standard shows that organisations are putting in effort and commitment towards security and improving their security posture through a well-defined continual improvement process. Although ISO 27001 certification remains non-mandatory for most organisations, organisations are beginning to recognise the value and benefits it brings in certifying the strength of its ISMS as it becomes the new norm for best practice in information security.
You might be wondering if ISO 27002 is a separate standard in the ISO 27000 series. Well, not exactly. Annex A provides an outline for each control, ISO 27002 delves into the details on how the controls can be implemented. The ISO 27002 standard, like all other ISO standards, is subject to a review every 5 years to determine whether updates are required. Since its last revision in 2013, ISO 27002 has been set for a refresh, and is slated to be published by end 2021.
Unlike ISO 27001, organisations cannot certify against ISO 27002. It is to be used as a reference for control implementation. Organisations can select additional controls from other standards such as PCI DSS, NIST or MITRE ATT&CK framework and so forth.
What has changed in ISO 27002?
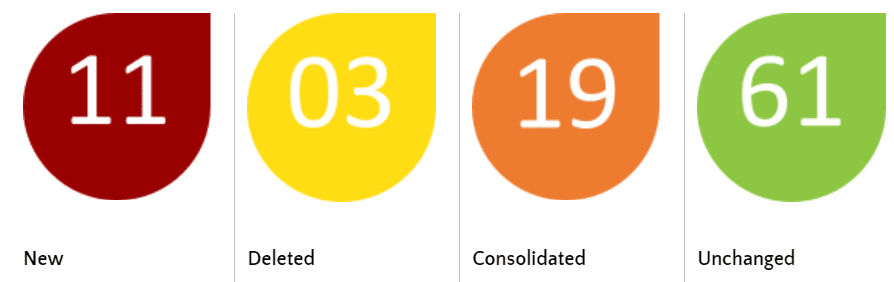
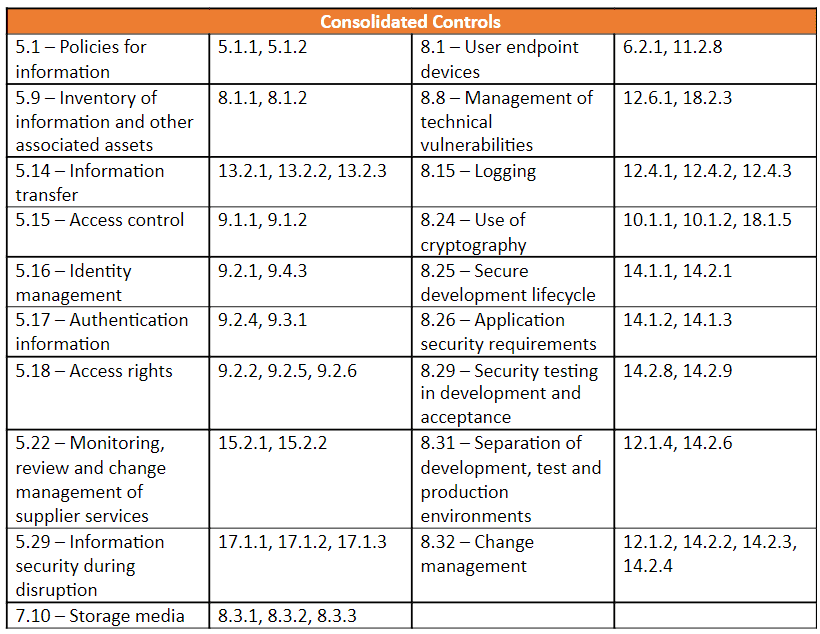
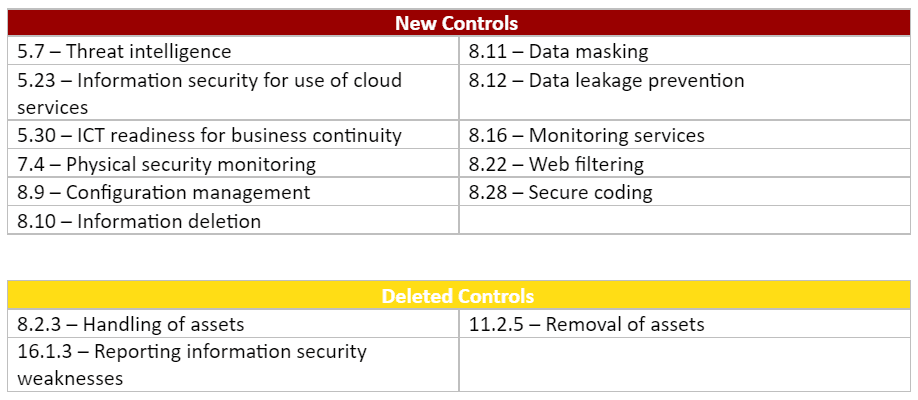
The main difference between the Draft International Standard (DIS) and the 2013 version is the structure of the control set. While majority of the ISO 27002 controls remains unchanged, the controls have been regrouped from 14 categories to 4 broad categories that include Organisational, People, Physical and Technology. The number of controls has also been reduced from 114 to 93 in the DIS, with the introduction of 11 new controls, deletion of 3 existing controls and consolidation of 48 controls into the current 19 controls.
For example, controls pertaining to user endpoint devices was distributed across different domains (A6 and A11) in the 2013 version, when it could be combined under one broad category (i.e., user endpoint devices) in the DIS. Some other individual controls in the 2013 version were also integrated into a single control in the DIS as they are work on the same fundamental principles. For example, controls A.12.4.1 to A.12.4.3 in the 2013 version which concerns logs have been categorised under Logging in DIS to minimise duplication. The wider structure eliminates redundancy between controls across multiple domains as well as within the same domain. It allows users to examine the subject based on themes and direct implementation efforts effectively. The new structure is less prescriptive and gives organisations the autonomy to explore its options to meet control objectives.
Digital transformation, together with a worsening cyber threat landscape, has accelerated the change in ISO 27002. ISO 27002 will include new controls relating to threat intelligence, cloud services and secure coding to reflect the rapidly evolving technology.
We can see similar updates to other industry standards and guidelines, such as the Monetary Authority of Singapore (MAS) Technology Risk Management (TRM) Guidelines in 2021 and the Association of Banks in Singapore (ABS) Cloud Computing Implementation Guide in 2019. The new MAS TRM guidelines has been updated to include best practices on cyber security operations and software application development and management while the ABS Cloud Computing Implementation Guide revised to place more emphasis on the safe adoption on cloud; all three topics new in ISO 27002 DIS. At a broader level, there are changes to regulations concerning data, especially personally identifiable information on the international field. Threat intelligence has also been included in industry guidelines published across several bodies, signalling an industry wide recognition of its value as part of a cyber defender’s arsenal.
With the pending updates to the ISO 27002, it is now more well-rounded for tackling information security risks. What remains a constant, is the purpose of the standard to provide implementation guidance on security best practices for compliance to ISO 27001.
The differences are summarized in the tables below:
How does the new revision of ISO 27002 impact ISO 27001?
Since ISO 27002 is essentially expanding on Annex A of ISO 27001, an update to ISO 27002 will inevitably affect the control set in ISO 27001. These changes are expected to be reflected in Annex A of ISO 27001 after the official release of the updated ISO 27002 to ensure that information from both standards is consistent.
How does it impact organisations that are already ISO-certified?
There is currently no impact on organisations that are already maintaining a certified ISMS until the ISO 27002 DIS has been finalised and the new ISO 27001 Annex A released. Typically, organisations will be given a grace period before they are required to adopt the revised ISO 27001 standard and it is likely for organisations to address the changes in conjunction with the next recertification audit cycle once the revised standard is published.
Although further modification is possible prior to formal publication, it might still be worthwhile for organisations to obtain a copy of the ISO 27002 DIS and access the impact of the changes to their existing ISMS implementation and the additional effort required to meet the updated requirements, so to better prepare themselves for the upcoming changes than to struggle with the implementation thereafter.
For organisations that intend to certify their ISMS, this should not be a showstopper. Organisations should familiarise themselves with the draft control set and with the help of the mapping to the 2013 version, make-ready for the certification.
What is the extended impact to other ISO standards?
Extended standards such as
- ISO 27017 – Code of practice for information security controls based on ISO/IEC 27002 for cloud services;
- ISO 27018 – Code of practice for protection of personally identifiable information (PII) in public clouds acting as PII processors; and
- ISO 27701 – Extension to ISO/IEC 27001 and ISO/IEC 27002 for privacy information management
will be affected by the revision of ISO 27002. At this stage, there is limited information on other standards that rely on ISO 27002 controls. However, this should not hinder organisations who are currently planning on obtaining certification or those who are operating and maintaining a certified ISMS.