By Matt Nicholas, Senior Consultant
Cyber attacks are increasing in frequency, sophistication, and impact, with perpetrators continually refining their efforts to compromise systems, networks, and information world-wide. Most organisations procure services from a third-party vendor/supplier. Vendors and suppliers can pose many risks including compliance, financial, legal, reputational and more. Therefore, it is always in a company’s best interest to protect itself from vendor risks – before entering, during, and even after the vendor relationship has been established.
Data breaches often originate from vendors and are rarely considered a risk. Not only are they frequent, but they are also increasingly costly. The average cost of a data breach involving a vendor is now close to AUD$2.70 million .
Globally, just under 30 per cent of organisations are likely to suffer at least one breach over the next 24 months. The size of the average data breach is now 34,249 data records, with the average cost of $141 per compromised record.
There has been an increase in cyber attacks and in particular the third-party vendor space. A high-profile example being SolarWinds, which provides software to help businesses manage their networks, systems and infrastructure. These companies were subjected to a large-scale cyber attack that impacted major companies like Microsoft, Cicso, Intel and government agencies. Hackers circumvented SolarWinds systems and added malicious code into these companies’ Orion software, which has around 33,000 customers. Customers were affected when SolarWinds unknowingly sent out software updates that included the malicious code, giving hackers a backdoor to customer systems, and allowing them to install malware to spy on companies and governmental agencies. The hack went undetected for months.

Do I still have your attention? As companies outsource their processes or services, they expose themselves to a wide range of risks, including data risk, business disruption, legal liability and compliance risk, all of which have a major impact on company profits and brand/reputational value. Companies and organisations tend to focus on securing the perimeter and with data only being as secure as the weakest link, third-party risk is considered once these types of breaches occur. Whether companies want to satisfy regulatory compliance, effectively manage customer queries, existing customers concerns or acquire new business opportunities, then building meaningful, beneficial, and operationally effective relationships with its third-party suppliers is imperative. It’s also essential to monitor its third parties more frequently and this is paramount to the success of the company/organisation.
This blog focuses on the cyber risk attached to partnering with third-party suppliers, but there are other areas of risk that should be considered when reviewing third parties, as depicted in figure 2.
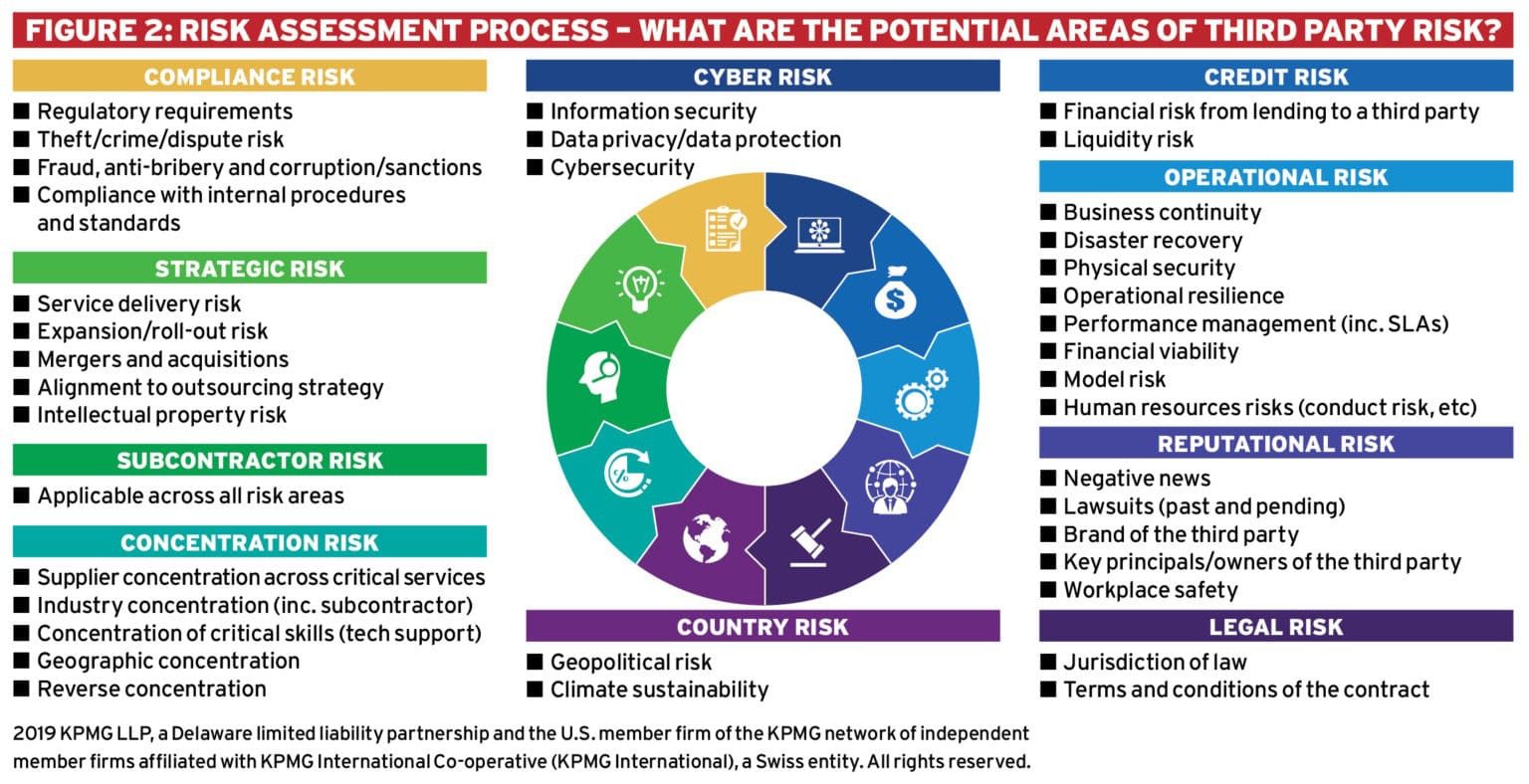
Third-party risk management (TPRM) must have a policy and a clear definition of the risk appetite within the third-party management space. Also, included is a definition of “third party” i.e., “business arrangement with another entity”, business requirements and frequency of assessments defined by the criticality.
It is crucial to embed the TPRM process into the procurement and legal tendering processes within the company/organisation, so the business can make risk-based decisions before entering into an agreement with a third party. It is also an opportunity to incorporate legally binding requirements into the contract based on the results of any third-party risk assessment.
TPRM is categorised into 4 separate areas:
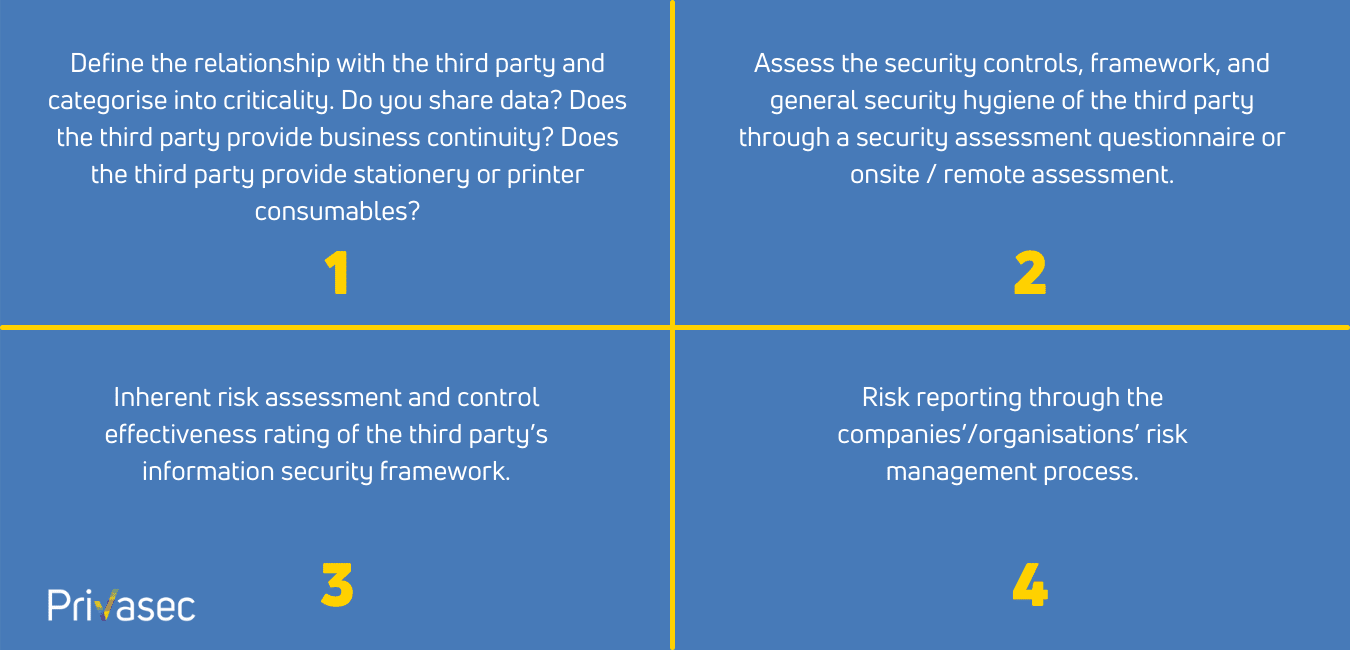
What about already onboarded suppliers? This is a good question, and with the TPRM process there are two streams:
- New supplier relationships
- Legacy onboarded relationship.
We need to understand the potential for new risk with potential new supplier relationships but also, and more critically, the existing risk profile of suppliers that we already have a relationship with. The key is to actively manage any risk, report and monitor for continual process improvement.
To effectively manage the growing risk profile in the third-party supplier space is to stay ahead of future challenges and proactively understand the risk to the organisation. Third-party risk management should be embedded in any company/organisation’s security framework.





















