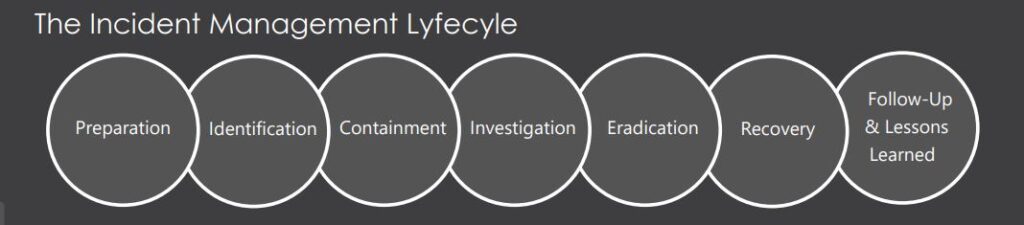
What does your organisation need: Penetration Test or Vulnerability Scan?
A vulnerability scan detects and classifies system weaknesses in computers, networks, and communications equipment. A penetration test, on the other hand, is the practice of testing a computer system, network or web application to identify insecure business processes, poor security settings, or other weaknesses that a hacker could exploit.