The Prelude: Understanding the Threat Landscape
The cybersecurity landscape is constantly evolving, and so is the sophistication of cyber threats. While the rapid acceleration in Artificial Intelligence development brings about exciting new possibilities for cybersecurity, it also introduces new threats like advanced phishing campaigns and deepfakes. New key trends such as global cloud adoption (multi-cloud predicted to hit 85% by 2024) and the growing risk of supply-chain attacks that exploit vendor-client relationships.
This blogpost dives deep into the anatomy of a cyber-attack, exploring each stage from initial breach to recovery and future preventions. By understanding these threats and implementing a strong robust incident response plan, organisations can adopt a more proactive defence cyber strategy that builds cyber resilience.
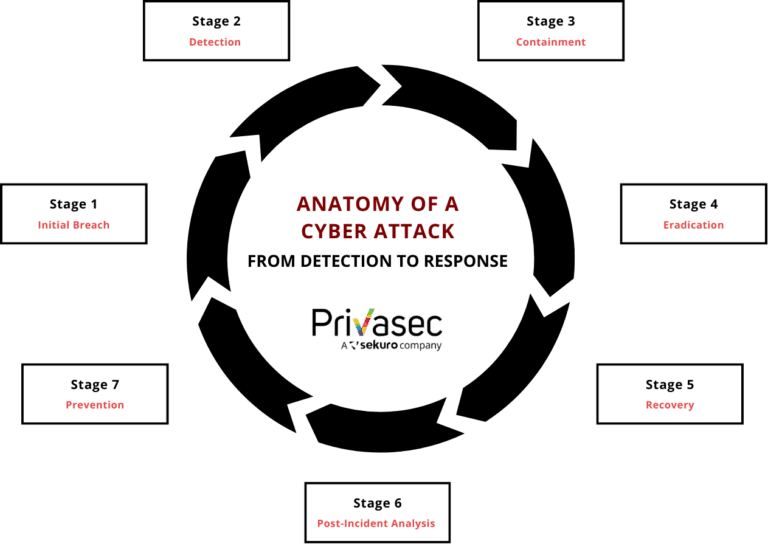
Stage 1 - Initial Breach: How the Attack Begins

Cyberattacks often start with a seemingly harmless event that targets a subtle crack in your organisation’s digital defences. Some examples include an employee clicking on a malicious link in a phishing email, outdated software with known vulnerabilities waiting to be exploited on a public server, or weak passwords that are easy prey for attackers. These seemingly innocuous breaches are all an attacker needs to establish a foothold in the system environment, creating a springboard for further intrusions.
Stage 2 - Detection: Identifying the Intrusion

Once an attacker has breached your organisation’s defences, the clock starts ticking. Early detection is the cornerstone of minimising damage from a cyberattack – the sooner the intrusion is discovered, the faster it can be contained. Security software alerts, flagging of unusual network traffic and employee awareness are some crucial ways to spot an attack early.
Your security arsenal is your first line of defence. Antivirus programs scan for known malware signature while Intrusion Detection Systems (IDS) continuously monitor network traffic for patterns that indicate malicious activities like port scans and brute force attacks. Endpoint Detection and Response (EDR) tools, on the other hand, take things a step further by monitoring individual devices for suspicious file activities, process executions or system behaviour.
Organisations should also be wary of sudden surges in network traffic or multiple access attempts from unauthorised locations. These anomalies might indicate ongoing malicious activity; hence, employees should remain vigilant and report suspicious emails, system behaviours or access attempts. An organisation’s employees are a valuable asset in fighting against cybercrimes and they play a vital role in early detection. Employees should be kept up to date with common cyber threats and trained to recognise key phishing email tell-tale signs such as grammatical errors, sender address inconsistencies and calls for urgent responses.
Stage 3 - Containment: Limiting the Damage

Swift action is crucial once a breach has been detected. Once a confirmed intrusion is identified, swift action should be taken to contain and isolate the threat to prevent further damage to the system environment. This may involve several steps such as isolating infected systems, revoking system access and shutting down critical infrastructure as a last resort.
In the first step, the organisation should isolate all compromised systems or network segments by quarantining infected devices. Think of this as building a digital wall, which cuts off the attacker’s ability to move laterally in the network and further infect other devices. Not only should devices be isolated, but access privileges also associated with compromised accounts should be revoked. In extreme dire circumstances, if containment measures are insufficient, it would be necessary for critical systems to be shut down to prevent further data exfiltration or system damage and disruptions.
Stage 4 Eradication: Removing the Threat

While containment focuses on stopping the attacker in their tracks, it is not the be-all and end-all. Eradication is the next decisive stage where an organisation should be taking steps to complete remove the threat actor and their tools from the environment.
This process involves several steps such as patching vulnerabilities, removing the malware and changing compromised credentials. During the eradication process, affected software and systems should be updated with the latest security patches to close exploited vulnerabilities, to prevent the attacker from re-exploiting the vulnerability and moving laterally within the network. Anti-malware software should be deployed to scan and remove malicious programs and scripts from infected systems, which should disable persistent mechanisms, such as hidden backdoors, used by the attacker to maintain access. Lastly, all compromised passwords should be reset to ensure the attacker cannot re-enter the system with the stolen credentials.
Stage 5 - Recovery: Getting Back to Business

While eradicating the threat is a strong victory, the job is not yet finished. After eradication, organisations should focus on business recovery and ensuring operations are running smoothly. This crucial stage entails data recovery and system restoration. By implementing efficient data recovery processes, critical information can be restored from backups to ensure a swift return to normal operations. Apart from data recovery, affected systems also need to be recovered to a clean and secure state. This involves re-imaging systems from clean backups and in some cases, manual cleaning of infected systems might be necessary. This creates a fresh and uninfected environment that is free from any residual malware before operations resume.
Stage 6 - Post-Incident Analysis: Learning from the Attack

While recovering from the attack is crucial, true progress comes from learning from the experience. A thorough post-incident analysis is essential in preventing similar breaches in the future. In the review process, the organisation should investigate the attack by meticulously analysing logs, network traffic and infected systems. By piecing these digital breadcrumbs together, the organisation’s security team can reconstruct the attacker’s tactics, techniques, and procedures (TTPs). Conducting an in-depth investigation helps identify the specific vulnerabilities exploited in the breach and pinpoint weaknesses in your existing security defences, which is the first step in identifying the gaps to optimize the security posture and prevent future intrusions.
Stage 7 - Prevention: Strengthening Defenses for the Future

All in all, cybersecurity is a continuous battle and vigilance is key. True victory lies in preventing future breaches by proactively strengthening your defences and building a more resilient security posture through regular security assessments, employee education and stronger access control policies.
Just like a building undergoing regular inspections, an organisation’s IT systems and networks need periodic security check-ups. Regular penetration testing and vulnerability assessments should be scheduled to identify and address weaknesses in the system, configurations, and security controls.
Additionally, employee education is critical to empower employees to become active participants in an organisation’s security strategy. Investing in regular security awareness training programs that cover best practices for password hygiene, email security, and reporting suspicious activity, equip employees with the knowledge to identify and report threats, which will significantly reduce the effectiveness of social engineering attacks.
By following these preventative measures and staying informed about evolving threats, an organisation can build a robust security posture and greatly reduce the risk of future cyberattacks. Organisations can consider conducting Tabletop Exercises (TTX) to simulate a cyberattack scenario and allow the team to walk through the steps of an attack, from initial breach to recovery. By testing the response plan in a controlled environment, an organisation can ensure a more efficient and coordinated response in the event of a real-world attack.